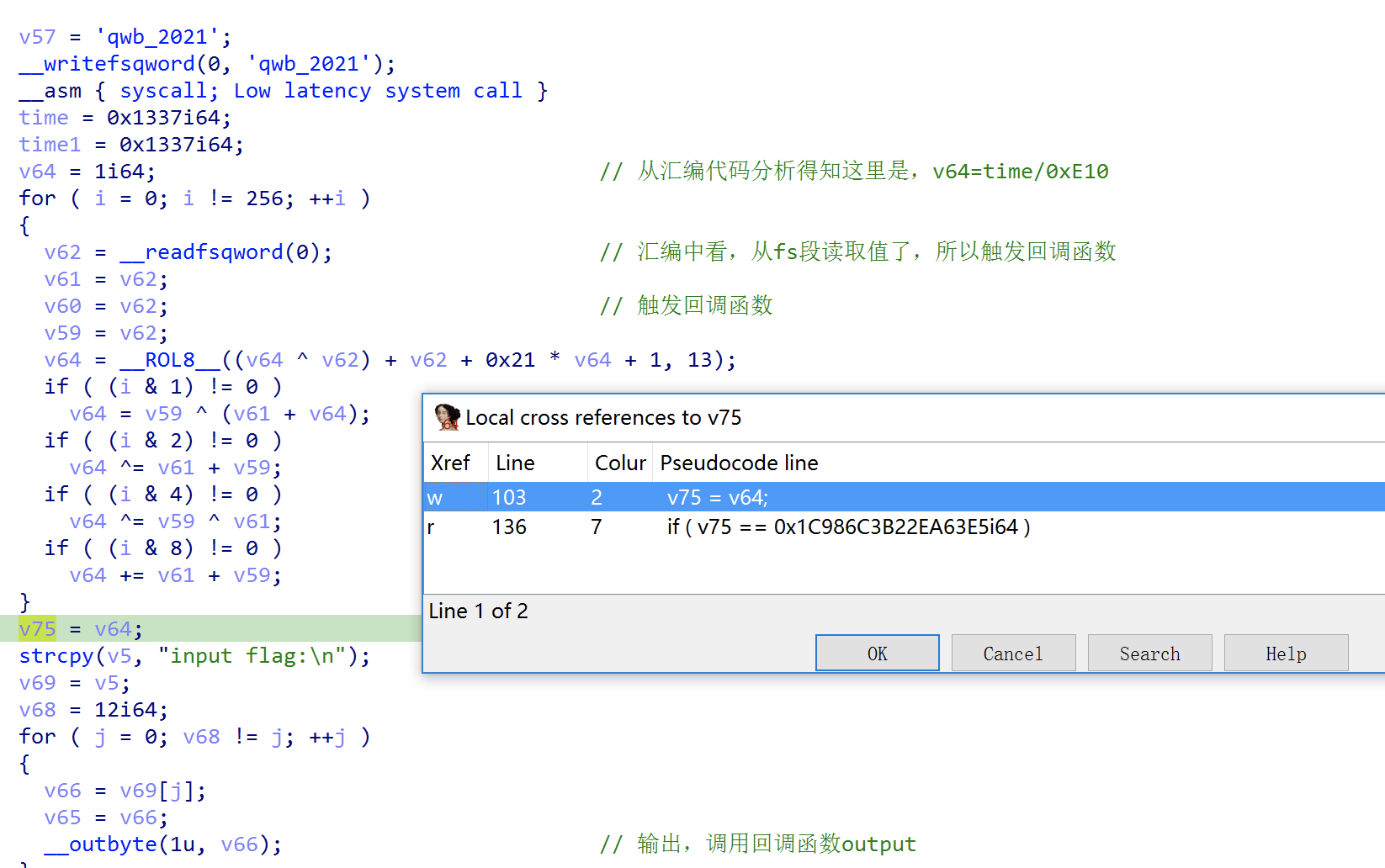
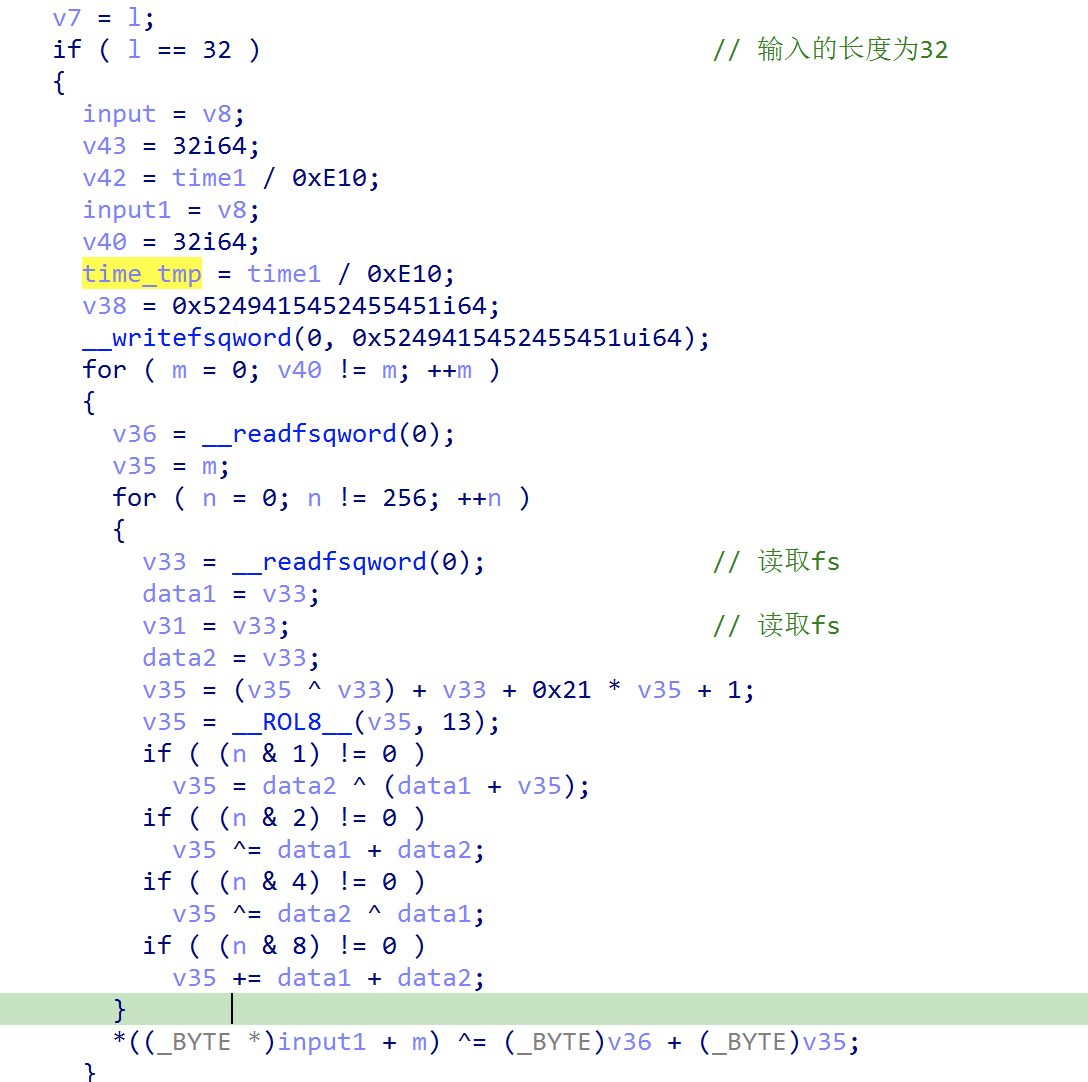
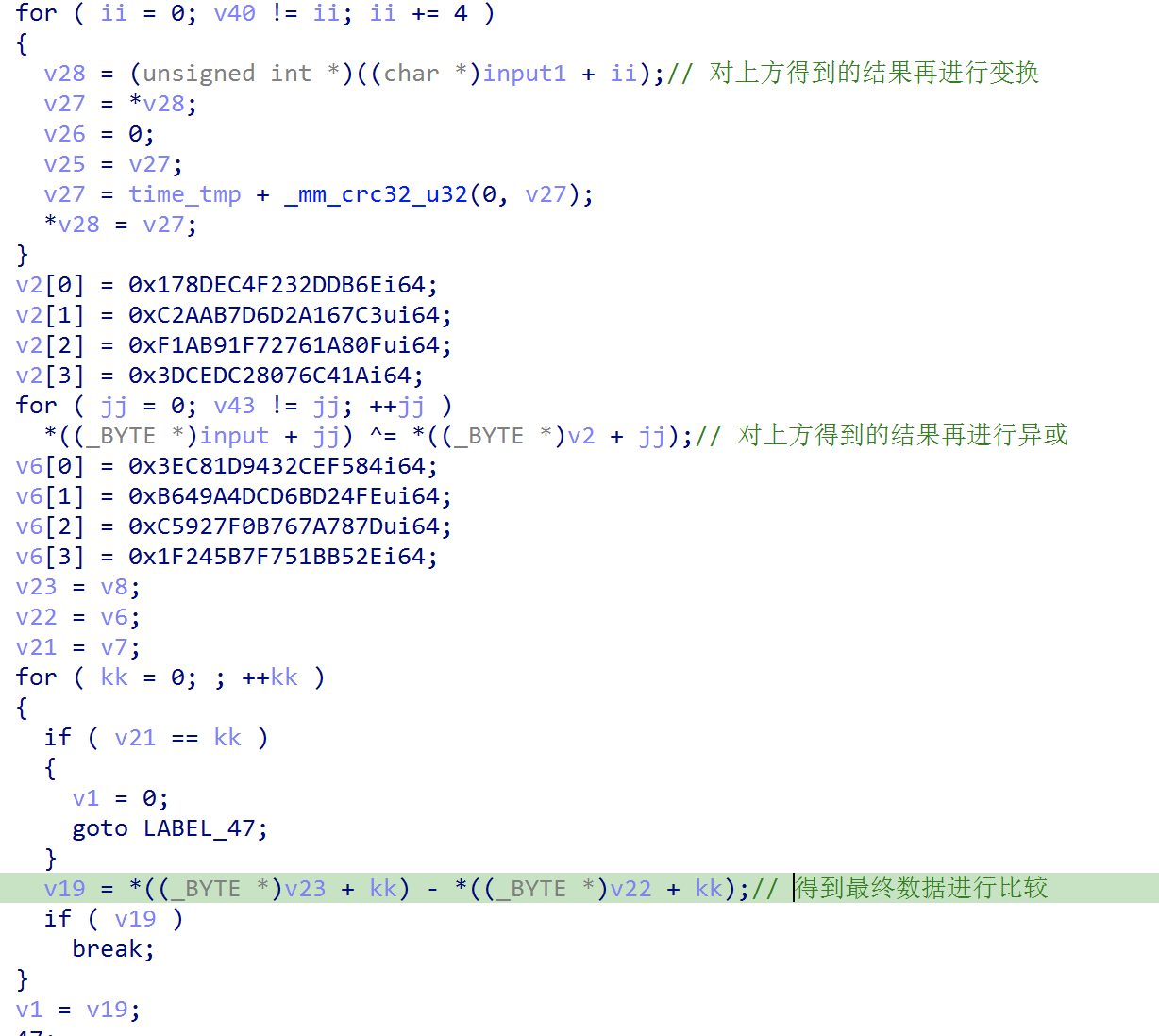
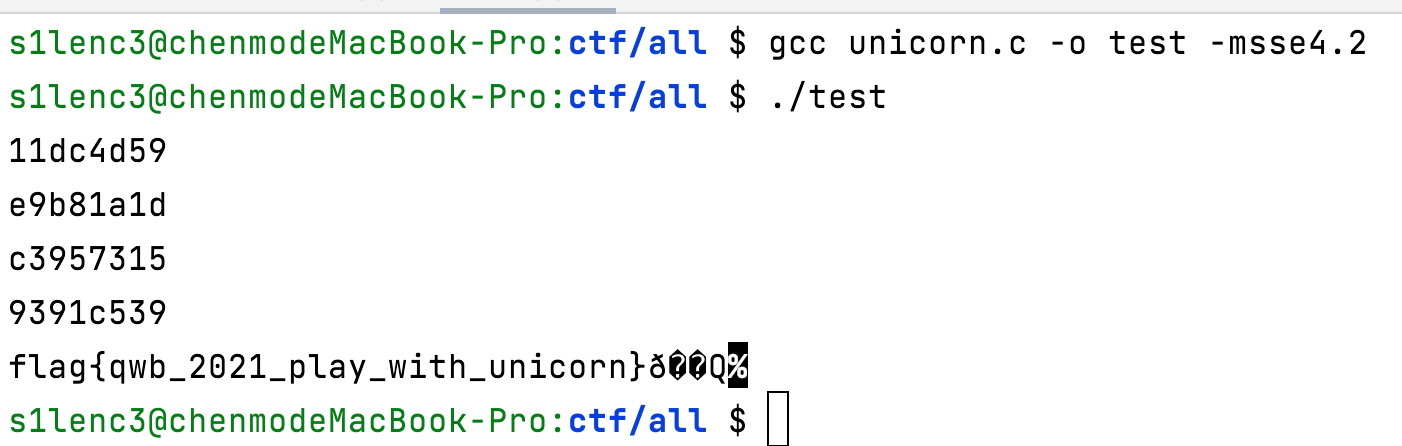
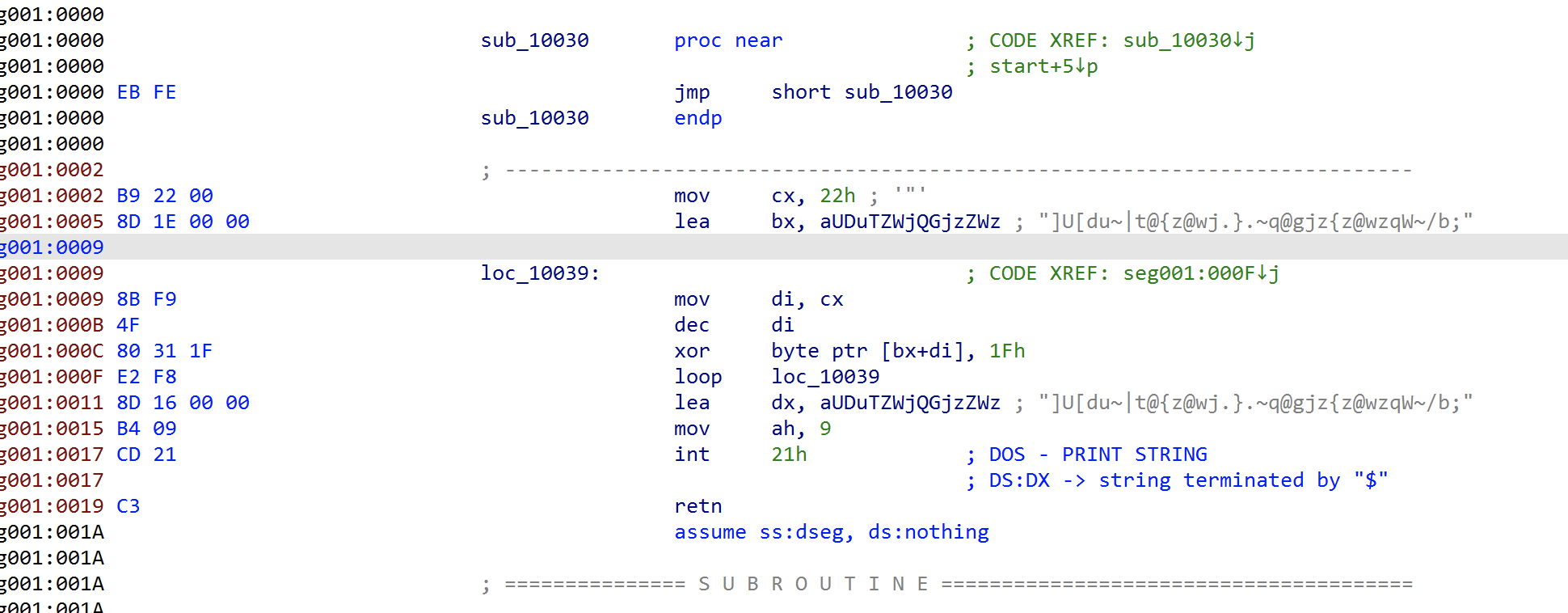
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
403
404
405
406
407
408
409
410
411
412
413
414
415
416
417
418
419
420
421
422
423
424
425
426
427
428
429
430
431
432
433
434
435
436
437
438
439
440
441
442
443
444
445
446
447
448
449
450
451
452
453
454
455
456
457
458
459
460
461
462
463
464
465
466
467
468
469
470
471
472
473
474
475
476
477
478
479
480
481
482
483
484
485
486
487
488
489
490
491
492
493
494
495
496
497
498
499
500
501
502
503
504
505
506
507
508
509
510
511
512
513
514
515
516
517
518
519
520
521
522
523
524
525
526
527
528
529
530
531
532
533
534
535
536
537
538
539
540
541
542
543
544
545
546
547
548
549
550
551
552
553
554
555
556
557
558
559
560
561
562
563
564
565
566
567
568
569
570
571
572
573
574
575
576
577
578
579
580
581
582
583
584
585
586
587
588
589
590
591
592
593
594
595
596
597
598
599
600
601
602
603
604
605
606
607
608
609
610
611
612
613
614
615
616
617
618
619
620
621
622
623
624
625
626
627
628
629
630
631
632
633
634
635
636
637
638
639
640
641
642
643
644
645
646
647
648
649
650
651
652
653
654
655
656
657
658
659
660
661
662
663
664
665
666
667
668
669
670
671
672
673
674
675
676
677
678
679
680
681
682
683
684
685
686
687
688
689
690
691
692
693
694
695
696
697
698
699
700
701
702
703
704
705
706
707
708
709
710
711
712
713
714
715
716
717
718
719
720
721
722
723
724
725
726
727
728
729
730
731
732
733
734
735
736
737
738
739
740
741
742
743
744
745
746
747
748
749
750
751
752
753
754
755
756
757
758
759
760
761
762
763
764
765
766
767
768
769
770
771
772
773
774
775
776
777
778
779
780
781
782
783
784
785
786
787
788
789
790
791
792
793
794
795
796
797
798
799
800
801
802
803
804
805
806
807
808
809
810
811
812
813
814
815
816
817
818
819
820
821
822
823
824
825
826
827
828
829
830
831
832
833
834
835
836
837
838
839
840
841
842
843
844
845
846
847
848
849
850
851
852
853
854
855
856
857
858
859
860
861
862
863
864
865
866
867
868
869
870
871
872
873
874
875
876
877
878
879
880
881
882
883
884
885
886
887
888
889
890
891
892
893
894
895
896
897
898
899
900
901
902
903
904
905
906
907
908
909
910
911
912
913
914
915
916
917
918
919
920
921
922
923
924
925
926
927
928
929
930
931
932
933
934
935
936
937
938
939
940
941
942
943
944
945
946
947
948
949
950
951
952
953
954
955
956
957
958
959
960
961
962
963
964
965
966
967
968
969
970
971
972
973
974
975
976
977
978
979
980
981
982
983
984
985
986
987
988
989
990
991
992
993
994
995
996
997
998
999
1000
1001
1002
1003
1004
1005
1006
1007
1008
1009
1010
1011
1012
1013
1014
1015
1016
1017
1018
1019
1020
1021
1022
1023
1024
1025
1026
1027
1028
1029
1030
1031
1032
1033
1034
1035
1036
1037
1038
1039
1040
1041
1042
1043
1044
1045
1046
1047
1048
1049
1050
1051
1052
1053
1054
1055
1056
1057
1058
1059
1060
1061
1062
1063
1064
1065
1066
1067
1068
1069
1070
1071
1072
1073
1074
1075
1076
1077
1078
1079
1080
1081
1082
1083
1084
1085
1086
1087
1088
1089
1090
1091
1092
1093
1094
1095
1096
1097
1098
1099
1100
1101
1102
1103
1104
1105
1106
1107
1108
1109
1110
1111
1112
1113
1114
1115
1116
1117
1118
1119
1120
1121
1122
1123
1124
1125
1126
1127
1128
1129
1130
1131
1132
1133
1134
1135
1136
1137
1138
1139
1140
1141
1142
1143
1144
1145
1146
1147
1148
1149
1150
1151
1152
1153
1154
1155
1156
1157
1158
1159
1160
1161
1162
1163
1164
1165
1166
1167
1168
1169
1170
1171
1172
1173
1174
1175
1176
1177
1178
1179
1180
1181
1182
1183
1184
1185
1186
1187
1188
1189
1190
1191
1192
1193
1194
1195
1196
1197
1198
1199
1200
1201
1202
1203
1204
1205
1206
1207
1208
1209
1210
1211
1212
1213
1214
1215
1216
1217
1218
1219
1220
1221
1222
1223
1224
1225
1226
1227
1228
1229
1230
1231
1232
1233
1234
1235
1236
1237
1238
1239
1240
1241
1242
1243
1244
1245
1246
1247
1248
1249
1250
1251
1252
1253
1254
1255
1256
1257
1258
1259
1260
1261
1262
1263
1264
1265
1266
1267
1268
1269
1270
1271
1272
1273
1274
1275
1276
1277
1278
1279
1280
1281
1282
1283
1284
1285
1286
1287
1288
1289
1290
1291
1292
1293
1294
1295
1296
1297
1298
1299
1300
1301
1302
1303
1304
1305
1306
1307
1308
1309
1310
1311
1312
1313
1314
1315
1316
1317
1318
1319
1320
1321
1322
1323
1324
1325
1326
1327
1328
1329
1330
1331
1332
1333
1334
1335
1336
1337
1338
1339
1340
1341
1342
1343
1344
1345
1346
1347
1348
1349
1350
1351
1352
1353
1354
1355
1356
1357
1358
1359
1360
1361
1362
1363
1364
1365
1366
1367
1368
1369
1370
1371
1372
1373
1374
1375
1376
1377
1378
1379
1380
1381
1382
1383
1384
1385
1386
1387
1388
1389
1390
1391
1392
1393
1394
1395
1396
| uc_err uc_hook_add(uc_engine *uc, uc_hook *hh, int type, void *callback,
void *user_data, uint64_t begin, uint64_t end, ...);
注册hook事件的回调,当hook事件被触发将会进行回调。
@uc: uc_open() 返回的句柄
@hh: 注册hook得到的句柄. uc_hook_del() 中使用
@type: hook 类型
@callback: 当指令被命中时要运行的回调
@user_data: 用户自定义数据. 将被传递给回调函数的最后一个参数 @user_data
@begin: 回调生效区域的起始地址(包括)
@end: 回调生效区域的结束地址(包括)
注意 1: 只有回调的地址在[@begin, @end]中才会调用回调
注意 2: 如果 @begin > @end, 每当触发此hook类型时都会调用回调
@...: 变量参数 (取决于 @type)
注意: 如果 @type = UC_HOOK_INSN, 这里是指令ID (如: UC_X86_INS_OUT)
@return 成功则返回UC_ERR_OK , 否则返回 uc_err 枚举的其他错误类型
uc_hook_type
uc_hook_add()的所有hook类型参数
typedef enum uc_hook_type {
UC_HOOK_INTR = 1 << 0,
UC_HOOK_INSN = 1 << 1,
UC_HOOK_CODE = 1 << 2,
UC_HOOK_BLOCK = 1 << 3,
UC_HOOK_MEM_READ_UNMAPPED = 1 << 4,
UC_HOOK_MEM_WRITE_UNMAPPED = 1 << 5,
UC_HOOK_MEM_FETCH_UNMAPPED = 1 << 6,
UC_HOOK_MEM_READ_PROT = 1 << 7,
UC_HOOK_MEM_WRITE_PROT = 1 << 8,
UC_HOOK_MEM_FETCH_PROT = 1 << 9,
UC_HOOK_MEM_READ = 1 << 10,
UC_HOOK_MEM_WRITE = 1 << 11,
UC_HOOK_MEM_FETCH = 1 << 12,
UC_HOOK_MEM_READ_AFTER = 1 << 13,
UC_HOOK_INSN_INVALID = 1 << 14,
} uc_hook_type;
typedef enum uc_x86_insn {
0 UC_X86_INS_INVALID = 0,
1 UC_X86_INS_AAA,
2 UC_X86_INS_AAD,
3 UC_X86_INS_AAM,
4 UC_X86_INS_AAS,
5 UC_X86_INS_FABS,
6 UC_X86_INS_ADC,
7 UC_X86_INS_ADCX,
8 UC_X86_INS_ADD,
9 UC_X86_INS_ADDPD,
10 UC_X86_INS_ADDPS,
11 UC_X86_INS_ADDSD,
12 UC_X86_INS_ADDSS,
13 UC_X86_INS_ADDSUBPD,
14 UC_X86_INS_ADDSUBPS,
15 UC_X86_INS_FADD,
16 UC_X86_INS_FIADD,
17 UC_X86_INS_FADDP,
18 UC_X86_INS_ADOX,
19 UC_X86_INS_AESDECLAST,
20 UC_X86_INS_AESDEC,
21 UC_X86_INS_AESENCLAST,
22 UC_X86_INS_AESENC,
23 UC_X86_INS_AESIMC,
24 UC_X86_INS_AESKEYGENASSIST,
25 UC_X86_INS_AND,
26 UC_X86_INS_ANDN,
27 UC_X86_INS_ANDNPD,
28 UC_X86_INS_ANDNPS,
29 UC_X86_INS_ANDPD,
30 UC_X86_INS_ANDPS,
31 UC_X86_INS_ARPL,
32 UC_X86_INS_BEXTR,
33 UC_X86_INS_BLCFILL,
34 UC_X86_INS_BLCI,
35 UC_X86_INS_BLCIC,
36 UC_X86_INS_BLCMSK,
37 UC_X86_INS_BLCS,
38 UC_X86_INS_BLENDPD,
39 UC_X86_INS_BLENDPS,
40 UC_X86_INS_BLENDVPD,
41 UC_X86_INS_BLENDVPS,
42 UC_X86_INS_BLSFILL,
43 UC_X86_INS_BLSI,
44 UC_X86_INS_BLSIC,
45 UC_X86_INS_BLSMSK,
46 UC_X86_INS_BLSR,
47 UC_X86_INS_BOUND,
48 UC_X86_INS_BSF,
49 UC_X86_INS_BSR,
50 UC_X86_INS_BSWAP,
51 UC_X86_INS_BT,
52 UC_X86_INS_BTC,
53 UC_X86_INS_BTR,
54 UC_X86_INS_BTS,
55 UC_X86_INS_BZHI,
56 UC_X86_INS_CALL,
57 UC_X86_INS_CBW,
58 UC_X86_INS_CDQ,
59 UC_X86_INS_CDQE,
60 UC_X86_INS_FCHS,
61 UC_X86_INS_CLAC,
62 UC_X86_INS_CLC,
63 UC_X86_INS_CLD,
64 UC_X86_INS_CLFLUSH,
65 UC_X86_INS_CLFLUSHOPT,
66 UC_X86_INS_CLGI,
67 UC_X86_INS_CLI,
68 UC_X86_INS_CLTS,
69 UC_X86_INS_CLWB,
70 UC_X86_INS_CMC,
71 UC_X86_INS_CMOVA,
72 UC_X86_INS_CMOVAE,
73 UC_X86_INS_CMOVB,
74 UC_X86_INS_CMOVBE,
75 UC_X86_INS_FCMOVBE,
76 UC_X86_INS_FCMOVB,
77 UC_X86_INS_CMOVE,
78 UC_X86_INS_FCMOVE,
79 UC_X86_INS_CMOVG,
80 UC_X86_INS_CMOVGE,
81 UC_X86_INS_CMOVL,
82 UC_X86_INS_CMOVLE,
83 UC_X86_INS_FCMOVNBE,
84 UC_X86_INS_FCMOVNB,
85 UC_X86_INS_CMOVNE,
86 UC_X86_INS_FCMOVNE,
87 UC_X86_INS_CMOVNO,
88 UC_X86_INS_CMOVNP,
89 UC_X86_INS_FCMOVNU,
90 UC_X86_INS_CMOVNS,
91 UC_X86_INS_CMOVO,
92 UC_X86_INS_CMOVP,
93 UC_X86_INS_FCMOVU,
94 UC_X86_INS_CMOVS,
95 UC_X86_INS_CMP,
96 UC_X86_INS_CMPPD,
97 UC_X86_INS_CMPPS,
98 UC_X86_INS_CMPSB,
99 UC_X86_INS_CMPSD,
100 UC_X86_INS_CMPSQ,
101 UC_X86_INS_CMPSS,
102 UC_X86_INS_CMPSW,
103 UC_X86_INS_CMPXCHG16B,
104 UC_X86_INS_CMPXCHG,
105 UC_X86_INS_CMPXCHG8B,
106 UC_X86_INS_COMISD,
107 UC_X86_INS_COMISS,
108 UC_X86_INS_FCOMP,
109 UC_X86_INS_FCOMPI,
110 UC_X86_INS_FCOMI,
111 UC_X86_INS_FCOM,
112 UC_X86_INS_FCOS,
113 UC_X86_INS_CPUID,
114 UC_X86_INS_CQO,
115 UC_X86_INS_CRC32,
116 UC_X86_INS_CVTDQ2PD,
117 UC_X86_INS_CVTDQ2PS,
118 UC_X86_INS_CVTPD2DQ,
119 UC_X86_INS_CVTPD2PS,
120 UC_X86_INS_CVTPS2DQ,
121 UC_X86_INS_CVTPS2PD,
122 UC_X86_INS_CVTSD2SI,
123 UC_X86_INS_CVTSD2SS,
124 UC_X86_INS_CVTSI2SD,
125 UC_X86_INS_CVTSI2SS,
126 UC_X86_INS_CVTSS2SD,
127 UC_X86_INS_CVTSS2SI,
128 UC_X86_INS_CVTTPD2DQ,
129 UC_X86_INS_CVTTPS2DQ,
130 UC_X86_INS_CVTTSD2SI,
131 UC_X86_INS_CVTTSS2SI,
132 UC_X86_INS_CWD,
133 UC_X86_INS_CWDE,
134 UC_X86_INS_DAA,
135 UC_X86_INS_DAS,
136 UC_X86_INS_DATA16,
137 UC_X86_INS_DEC,
138 UC_X86_INS_DIV,
139 UC_X86_INS_DIVPD,
140 UC_X86_INS_DIVPS,
141 UC_X86_INS_FDIVR,
142 UC_X86_INS_FIDIVR,
143 UC_X86_INS_FDIVRP,
144 UC_X86_INS_DIVSD,
145 UC_X86_INS_DIVSS,
146 UC_X86_INS_FDIV,
147 UC_X86_INS_FIDIV,
148 UC_X86_INS_FDIVP,
149 UC_X86_INS_DPPD,
150 UC_X86_INS_DPPS,
151 UC_X86_INS_RET,
152 UC_X86_INS_ENCLS,
153 UC_X86_INS_ENCLU,
154 UC_X86_INS_ENTER,
155 UC_X86_INS_EXTRACTPS,
156 UC_X86_INS_EXTRQ,
157 UC_X86_INS_F2XM1,
158 UC_X86_INS_LCALL,
159 UC_X86_INS_LJMP,
160 UC_X86_INS_FBLD,
161 UC_X86_INS_FBSTP,
162 UC_X86_INS_FCOMPP,
163 UC_X86_INS_FDECSTP,
164 UC_X86_INS_FEMMS,
165 UC_X86_INS_FFREE,
166 UC_X86_INS_FICOM,
167 UC_X86_INS_FICOMP,
168 UC_X86_INS_FINCSTP,
169 UC_X86_INS_FLDCW,
170 UC_X86_INS_FLDENV,
171 UC_X86_INS_FLDL2E,
172 UC_X86_INS_FLDL2T,
173 UC_X86_INS_FLDLG2,
174 UC_X86_INS_FLDLN2,
175 UC_X86_INS_FLDPI,
176 UC_X86_INS_FNCLEX,
177 UC_X86_INS_FNINIT,
178 UC_X86_INS_FNOP,
179 UC_X86_INS_FNSTCW,
180 UC_X86_INS_FNSTSW,
181 UC_X86_INS_FPATAN,
182 UC_X86_INS_FPREM,
183 UC_X86_INS_FPREM1,
184 UC_X86_INS_FPTAN,
185 UC_X86_INS_FFREEP,
186 UC_X86_INS_FRNDINT,
187 UC_X86_INS_FRSTOR,
188 UC_X86_INS_FNSAVE,
189 UC_X86_INS_FSCALE,
190 UC_X86_INS_FSETPM,
191 UC_X86_INS_FSINCOS,
192 UC_X86_INS_FNSTENV,
193 UC_X86_INS_FXAM,
194 UC_X86_INS_FXRSTOR,
195 UC_X86_INS_FXRSTOR64,
196 UC_X86_INS_FXSAVE,
197 UC_X86_INS_FXSAVE64,
198 UC_X86_INS_FXTRACT,
199 UC_X86_INS_FYL2X,
200 UC_X86_INS_FYL2XP1,
201 UC_X86_INS_MOVAPD,
202 UC_X86_INS_MOVAPS,
203 UC_X86_INS_ORPD,
204 UC_X86_INS_ORPS,
205 UC_X86_INS_VMOVAPD,
206 UC_X86_INS_VMOVAPS,
207 UC_X86_INS_XORPD,
208 UC_X86_INS_XORPS,
209 UC_X86_INS_GETSEC,
210 UC_X86_INS_HADDPD,
211 UC_X86_INS_HADDPS,
212 UC_X86_INS_HLT,
213 UC_X86_INS_HSUBPD,
214 UC_X86_INS_HSUBPS,
215 UC_X86_INS_IDIV,
216 UC_X86_INS_FILD,
217 UC_X86_INS_IMUL,
218 UC_X86_INS_IN,
219 UC_X86_INS_INC,
220 UC_X86_INS_INSB,
221 UC_X86_INS_INSERTPS,
222 UC_X86_INS_INSERTQ,
223 UC_X86_INS_INSD,
224 UC_X86_INS_INSW,
225 UC_X86_INS_INT,
226 UC_X86_INS_INT1,
227 UC_X86_INS_INT3,
228 UC_X86_INS_INTO,
229 UC_X86_INS_INVD,
230 UC_X86_INS_INVEPT,
231 UC_X86_INS_INVLPG,
232 UC_X86_INS_INVLPGA,
233 UC_X86_INS_INVPCID,
234 UC_X86_INS_INVVPID,
235 UC_X86_INS_IRET,
236 UC_X86_INS_IRETD,
237 UC_X86_INS_IRETQ,
238 UC_X86_INS_FISTTP,
239 UC_X86_INS_FIST,
240 UC_X86_INS_FISTP,
241 UC_X86_INS_UCOMISD,
242 UC_X86_INS_UCOMISS,
243 UC_X86_INS_VCOMISD,
244 UC_X86_INS_VCOMISS,
245 UC_X86_INS_VCVTSD2SS,
246 UC_X86_INS_VCVTSI2SD,
247 UC_X86_INS_VCVTSI2SS,
248 UC_X86_INS_VCVTSS2SD,
249 UC_X86_INS_VCVTTSD2SI,
250 UC_X86_INS_VCVTTSD2USI,
251 UC_X86_INS_VCVTTSS2SI,
252 UC_X86_INS_VCVTTSS2USI,
253 UC_X86_INS_VCVTUSI2SD,
254 UC_X86_INS_VCVTUSI2SS,
255 UC_X86_INS_VUCOMISD,
256 UC_X86_INS_VUCOMISS,
257 UC_X86_INS_JAE,
258 UC_X86_INS_JA,
259 UC_X86_INS_JBE,
260 UC_X86_INS_JB,
261 UC_X86_INS_JCXZ,
262 UC_X86_INS_JECXZ,
263 UC_X86_INS_JE,
264 UC_X86_INS_JGE,
265 UC_X86_INS_JG,
266 UC_X86_INS_JLE,
267 UC_X86_INS_JL,
268 UC_X86_INS_JMP,
269 UC_X86_INS_JNE,
270 UC_X86_INS_JNO,
271 UC_X86_INS_JNP,
272 UC_X86_INS_JNS,
273 UC_X86_INS_JO,
274 UC_X86_INS_JP,
275 UC_X86_INS_JRCXZ,
276 UC_X86_INS_JS,
277 UC_X86_INS_KANDB,
278 UC_X86_INS_KANDD,
279 UC_X86_INS_KANDNB,
280 UC_X86_INS_KANDND,
281 UC_X86_INS_KANDNQ,
282 UC_X86_INS_KANDNW,
283 UC_X86_INS_KANDQ,
284 UC_X86_INS_KANDW,
285 UC_X86_INS_KMOVB,
286 UC_X86_INS_KMOVD,
287 UC_X86_INS_KMOVQ,
288 UC_X86_INS_KMOVW,
289 UC_X86_INS_KNOTB,
290 UC_X86_INS_KNOTD,
291 UC_X86_INS_KNOTQ,
292 UC_X86_INS_KNOTW,
293 UC_X86_INS_KORB,
294 UC_X86_INS_KORD,
295 UC_X86_INS_KORQ,
296 UC_X86_INS_KORTESTB,
297 UC_X86_INS_KORTESTD,
298 UC_X86_INS_KORTESTQ,
299 UC_X86_INS_KORTESTW,
300 UC_X86_INS_KORW,
301 UC_X86_INS_KSHIFTLB,
302 UC_X86_INS_KSHIFTLD,
303 UC_X86_INS_KSHIFTLQ,
304 UC_X86_INS_KSHIFTLW,
305 UC_X86_INS_KSHIFTRB,
306 UC_X86_INS_KSHIFTRD,
307 UC_X86_INS_KSHIFTRQ,
308 UC_X86_INS_KSHIFTRW,
309 UC_X86_INS_KUNPCKBW,
310 UC_X86_INS_KXNORB,
311 UC_X86_INS_KXNORD,
312 UC_X86_INS_KXNORQ,
313 UC_X86_INS_KXNORW,
314 UC_X86_INS_KXORB,
315 UC_X86_INS_KXORD,
316 UC_X86_INS_KXORQ,
317 UC_X86_INS_KXORW,
318 UC_X86_INS_LAHF,
319 UC_X86_INS_LAR,
320 UC_X86_INS_LDDQU,
321 UC_X86_INS_LDMXCSR,
322 UC_X86_INS_LDS,
323 UC_X86_INS_FLDZ,
324 UC_X86_INS_FLD1,
325 UC_X86_INS_FLD,
326 UC_X86_INS_LEA,
327 UC_X86_INS_LEAVE,
328 UC_X86_INS_LES,
329 UC_X86_INS_LFENCE,
330 UC_X86_INS_LFS,
331 UC_X86_INS_LGDT,
332 UC_X86_INS_LGS,
333 UC_X86_INS_LIDT,
334 UC_X86_INS_LLDT,
335 UC_X86_INS_LMSW,
336 UC_X86_INS_OR,
337 UC_X86_INS_SUB,
338 UC_X86_INS_XOR,
339 UC_X86_INS_LODSB,
340 UC_X86_INS_LODSD,
341 UC_X86_INS_LODSQ,
342 UC_X86_INS_LODSW,
343 UC_X86_INS_LOOP,
344 UC_X86_INS_LOOPE,
345 UC_X86_INS_LOOPNE,
346 UC_X86_INS_RETF,
347 UC_X86_INS_RETFQ,
348 UC_X86_INS_LSL,
349 UC_X86_INS_LSS,
350 UC_X86_INS_LTR,
351 UC_X86_INS_XADD,
352 UC_X86_INS_LZCNT,
353 UC_X86_INS_MASKMOVDQU,
354 UC_X86_INS_MAXPD,
355 UC_X86_INS_MAXPS,
356 UC_X86_INS_MAXSD,
357 UC_X86_INS_MAXSS,
358 UC_X86_INS_MFENCE,
359 UC_X86_INS_MINPD,
360 UC_X86_INS_MINPS,
361 UC_X86_INS_MINSD,
362 UC_X86_INS_MINSS,
363 UC_X86_INS_CVTPD2PI,
364 UC_X86_INS_CVTPI2PD,
365 UC_X86_INS_CVTPI2PS,
366 UC_X86_INS_CVTPS2PI,
367 UC_X86_INS_CVTTPD2PI,
368 UC_X86_INS_CVTTPS2PI,
369 UC_X86_INS_EMMS,
370 UC_X86_INS_MASKMOVQ,
371 UC_X86_INS_MOVD,
372 UC_X86_INS_MOVDQ2Q,
373 UC_X86_INS_MOVNTQ,
374 UC_X86_INS_MOVQ2DQ,
375 UC_X86_INS_MOVQ,
376 UC_X86_INS_PABSB,
377 UC_X86_INS_PABSD,
378 UC_X86_INS_PABSW,
379 UC_X86_INS_PACKSSDW,
380 UC_X86_INS_PACKSSWB,
381 UC_X86_INS_PACKUSWB,
382 UC_X86_INS_PADDB,
383 UC_X86_INS_PADDD,
384 UC_X86_INS_PADDQ,
385 UC_X86_INS_PADDSB,
386 UC_X86_INS_PADDSW,
387 UC_X86_INS_PADDUSB,
388 UC_X86_INS_PADDUSW,
389 UC_X86_INS_PADDW,
390 UC_X86_INS_PALIGNR,
391 UC_X86_INS_PANDN,
392 UC_X86_INS_PAND,
393 UC_X86_INS_PAVGB,
394 UC_X86_INS_PAVGW,
395 UC_X86_INS_PCMPEQB,
396 UC_X86_INS_PCMPEQD,
397 UC_X86_INS_PCMPEQW,
398 UC_X86_INS_PCMPGTB,
399 UC_X86_INS_PCMPGTD,
400 UC_X86_INS_PCMPGTW,
401 UC_X86_INS_PEXTRW,
402 UC_X86_INS_PHADDSW,
403 UC_X86_INS_PHADDW,
404 UC_X86_INS_PHADDD,
405 UC_X86_INS_PHSUBD,
406 UC_X86_INS_PHSUBSW,
407 UC_X86_INS_PHSUBW,
408 UC_X86_INS_PINSRW,
409 UC_X86_INS_PMADDUBSW,
410 UC_X86_INS_PMADDWD,
411 UC_X86_INS_PMAXSW,
412 UC_X86_INS_PMAXUB,
413 UC_X86_INS_PMINSW,
414 UC_X86_INS_PMINUB,
415 UC_X86_INS_PMOVMSKB,
416 UC_X86_INS_PMULHRSW,
417 UC_X86_INS_PMULHUW,
418 UC_X86_INS_PMULHW,
419 UC_X86_INS_PMULLW,
420 UC_X86_INS_PMULUDQ,
421 UC_X86_INS_POR,
422 UC_X86_INS_PSADBW,
423 UC_X86_INS_PSHUFB,
424 UC_X86_INS_PSHUFW,
425 UC_X86_INS_PSIGNB,
426 UC_X86_INS_PSIGND,
427 UC_X86_INS_PSIGNW,
428 UC_X86_INS_PSLLD,
429 UC_X86_INS_PSLLQ,
430 UC_X86_INS_PSLLW,
431 UC_X86_INS_PSRAD,
432 UC_X86_INS_PSRAW,
433 UC_X86_INS_PSRLD,
434 UC_X86_INS_PSRLQ,
435 UC_X86_INS_PSRLW,
436 UC_X86_INS_PSUBB,
437 UC_X86_INS_PSUBD,
438 UC_X86_INS_PSUBQ,
439 UC_X86_INS_PSUBSB,
440 UC_X86_INS_PSUBSW,
441 UC_X86_INS_PSUBUSB,
442 UC_X86_INS_PSUBUSW,
443 UC_X86_INS_PSUBW,
444 UC_X86_INS_PUNPCKHBW,
445 UC_X86_INS_PUNPCKHDQ,
446 UC_X86_INS_PUNPCKHWD,
447 UC_X86_INS_PUNPCKLBW,
448 UC_X86_INS_PUNPCKLDQ,
449 UC_X86_INS_PUNPCKLWD,
450 UC_X86_INS_PXOR,
451 UC_X86_INS_MONITOR,
452 UC_X86_INS_MONTMUL,
453 UC_X86_INS_MOV,
454 UC_X86_INS_MOVABS,
455 UC_X86_INS_MOVBE,
456 UC_X86_INS_MOVDDUP,
457 UC_X86_INS_MOVDQA,
458 UC_X86_INS_MOVDQU,
459 UC_X86_INS_MOVHLPS,
460 UC_X86_INS_MOVHPD,
461 UC_X86_INS_MOVHPS,
462 UC_X86_INS_MOVLHPS,
463 UC_X86_INS_MOVLPD,
464 UC_X86_INS_MOVLPS,
465 UC_X86_INS_MOVMSKPD,
466 UC_X86_INS_MOVMSKPS,
467 UC_X86_INS_MOVNTDQA,
468 UC_X86_INS_MOVNTDQ,
469 UC_X86_INS_MOVNTI,
470 UC_X86_INS_MOVNTPD,
471 UC_X86_INS_MOVNTPS,
472 UC_X86_INS_MOVNTSD,
473 UC_X86_INS_MOVNTSS,
474 UC_X86_INS_MOVSB,
475 UC_X86_INS_MOVSD,
476 UC_X86_INS_MOVSHDUP,
477 UC_X86_INS_MOVSLDUP,
478 UC_X86_INS_MOVSQ,
479 UC_X86_INS_MOVSS,
480 UC_X86_INS_MOVSW,
481 UC_X86_INS_MOVSX,
482 UC_X86_INS_MOVSXD,
483 UC_X86_INS_MOVUPD,
484 UC_X86_INS_MOVUPS,
485 UC_X86_INS_MOVZX,
486 UC_X86_INS_MPSADBW,
487 UC_X86_INS_MUL,
488 UC_X86_INS_MULPD,
489 UC_X86_INS_MULPS,
490 UC_X86_INS_MULSD,
491 UC_X86_INS_MULSS,
492 UC_X86_INS_MULX,
493 UC_X86_INS_FMUL,
494 UC_X86_INS_FIMUL,
495 UC_X86_INS_FMULP,
496 UC_X86_INS_MWAIT,
497 UC_X86_INS_NEG,
498 UC_X86_INS_NOP,
499 UC_X86_INS_NOT,
500 UC_X86_INS_OUT,
501 UC_X86_INS_OUTSB,
502 UC_X86_INS_OUTSD,
503 UC_X86_INS_OUTSW,
504 UC_X86_INS_PACKUSDW,
505 UC_X86_INS_PAUSE,
506 UC_X86_INS_PAVGUSB,
507 UC_X86_INS_PBLENDVB,
508 UC_X86_INS_PBLENDW,
509 UC_X86_INS_PCLMULQDQ,
510 UC_X86_INS_PCMPEQQ,
511 UC_X86_INS_PCMPESTRI,
512 UC_X86_INS_PCMPESTRM,
513 UC_X86_INS_PCMPGTQ,
514 UC_X86_INS_PCMPISTRI,
515 UC_X86_INS_PCMPISTRM,
516 UC_X86_INS_PCOMMIT,
517 UC_X86_INS_PDEP,
518 UC_X86_INS_PEXT,
519 UC_X86_INS_PEXTRB,
520 UC_X86_INS_PEXTRD,
521 UC_X86_INS_PEXTRQ,
522 UC_X86_INS_PF2ID,
523 UC_X86_INS_PF2IW,
524 UC_X86_INS_PFACC,
525 UC_X86_INS_PFADD,
526 UC_X86_INS_PFCMPEQ,
527 UC_X86_INS_PFCMPGE,
528 UC_X86_INS_PFCMPGT,
529 UC_X86_INS_PFMAX,
530 UC_X86_INS_PFMIN,
531 UC_X86_INS_PFMUL,
532 UC_X86_INS_PFNACC,
533 UC_X86_INS_PFPNACC,
534 UC_X86_INS_PFRCPIT1,
535 UC_X86_INS_PFRCPIT2,
536 UC_X86_INS_PFRCP,
537 UC_X86_INS_PFRSQIT1,
538 UC_X86_INS_PFRSQRT,
539 UC_X86_INS_PFSUBR,
540 UC_X86_INS_PFSUB,
541 UC_X86_INS_PHMINPOSUW,
542 UC_X86_INS_PI2FD,
543 UC_X86_INS_PI2FW,
544 UC_X86_INS_PINSRB,
545 UC_X86_INS_PINSRD,
546 UC_X86_INS_PINSRQ,
547 UC_X86_INS_PMAXSB,
548 UC_X86_INS_PMAXSD,
549 UC_X86_INS_PMAXUD,
550 UC_X86_INS_PMAXUW,
551 UC_X86_INS_PMINSB,
552 UC_X86_INS_PMINSD,
553 UC_X86_INS_PMINUD,
554 UC_X86_INS_PMINUW,
555 UC_X86_INS_PMOVSXBD,
556 UC_X86_INS_PMOVSXBQ,
557 UC_X86_INS_PMOVSXBW,
558 UC_X86_INS_PMOVSXDQ,
559 UC_X86_INS_PMOVSXWD,
560 UC_X86_INS_PMOVSXWQ,
561 UC_X86_INS_PMOVZXBD,
562 UC_X86_INS_PMOVZXBQ,
563 UC_X86_INS_PMOVZXBW,
564 UC_X86_INS_PMOVZXDQ,
565 UC_X86_INS_PMOVZXWD,
566 UC_X86_INS_PMOVZXWQ,
567 UC_X86_INS_PMULDQ,
568 UC_X86_INS_PMULHRW,
569 UC_X86_INS_PMULLD,
570 UC_X86_INS_POP,
571 UC_X86_INS_POPAW,
572 UC_X86_INS_POPAL,
573 UC_X86_INS_POPCNT,
574 UC_X86_INS_POPF,
575 UC_X86_INS_POPFD,
576 UC_X86_INS_POPFQ,
577 UC_X86_INS_PREFETCH,
578 UC_X86_INS_PREFETCHNTA,
579 UC_X86_INS_PREFETCHT0,
580 UC_X86_INS_PREFETCHT1,
581 UC_X86_INS_PREFETCHT2,
582 UC_X86_INS_PREFETCHW,
583 UC_X86_INS_PSHUFD,
584 UC_X86_INS_PSHUFHW,
585 UC_X86_INS_PSHUFLW,
586 UC_X86_INS_PSLLDQ,
587 UC_X86_INS_PSRLDQ,
588 UC_X86_INS_PSWAPD,
589 UC_X86_INS_PTEST,
590 UC_X86_INS_PUNPCKHQDQ,
591 UC_X86_INS_PUNPCKLQDQ,
592 UC_X86_INS_PUSH,
593 UC_X86_INS_PUSHAW,
594 UC_X86_INS_PUSHAL,
595 UC_X86_INS_PUSHF,
596 UC_X86_INS_PUSHFD,
597 UC_X86_INS_PUSHFQ,
598 UC_X86_INS_RCL,
599 UC_X86_INS_RCPPS,
600 UC_X86_INS_RCPSS,
601 UC_X86_INS_RCR,
602 UC_X86_INS_RDFSBASE,
603 UC_X86_INS_RDGSBASE,
604 UC_X86_INS_RDMSR,
605 UC_X86_INS_RDPMC,
606 UC_X86_INS_RDRAND,
607 UC_X86_INS_RDSEED,
608 UC_X86_INS_RDTSC,
609 UC_X86_INS_RDTSCP,
610 UC_X86_INS_ROL,
611 UC_X86_INS_ROR,
612 UC_X86_INS_RORX,
613 UC_X86_INS_ROUNDPD,
614 UC_X86_INS_ROUNDPS,
615 UC_X86_INS_ROUNDSD,
616 UC_X86_INS_ROUNDSS,
617 UC_X86_INS_RSM,
618 UC_X86_INS_RSQRTPS,
619 UC_X86_INS_RSQRTSS,
620 UC_X86_INS_SAHF,
621 UC_X86_INS_SAL,
622 UC_X86_INS_SALC,
623 UC_X86_INS_SAR,
624 UC_X86_INS_SARX,
625 UC_X86_INS_SBB,
626 UC_X86_INS_SCASB,
627 UC_X86_INS_SCASD,
628 UC_X86_INS_SCASQ,
629 UC_X86_INS_SCASW,
630 UC_X86_INS_SETAE,
631 UC_X86_INS_SETA,
632 UC_X86_INS_SETBE,
633 UC_X86_INS_SETB,
634 UC_X86_INS_SETE,
635 UC_X86_INS_SETGE,
636 UC_X86_INS_SETG,
637 UC_X86_INS_SETLE,
638 UC_X86_INS_SETL,
639 UC_X86_INS_SETNE,
640 UC_X86_INS_SETNO,
641 UC_X86_INS_SETNP,
642 UC_X86_INS_SETNS,
643 UC_X86_INS_SETO,
644 UC_X86_INS_SETP,
645 UC_X86_INS_SETS,
646 UC_X86_INS_SFENCE,
647 UC_X86_INS_SGDT,
648 UC_X86_INS_SHA1MSG1,
649 UC_X86_INS_SHA1MSG2,
650 UC_X86_INS_SHA1NEXTE,
651 UC_X86_INS_SHA1RNDS4,
652 UC_X86_INS_SHA256MSG1,
653 UC_X86_INS_SHA256MSG2,
654 UC_X86_INS_SHA256RNDS2,
655 UC_X86_INS_SHL,
656 UC_X86_INS_SHLD,
657 UC_X86_INS_SHLX,
658 UC_X86_INS_SHR,
659 UC_X86_INS_SHRD,
660 UC_X86_INS_SHRX,
661 UC_X86_INS_SHUFPD,
662 UC_X86_INS_SHUFPS,
663 UC_X86_INS_SIDT,
664 UC_X86_INS_FSIN,
665 UC_X86_INS_SKINIT,
666 UC_X86_INS_SLDT,
667 UC_X86_INS_SMSW,
668 UC_X86_INS_SQRTPD,
669 UC_X86_INS_SQRTPS,
670 UC_X86_INS_SQRTSD,
671 UC_X86_INS_SQRTSS,
672 UC_X86_INS_FSQRT,
673 UC_X86_INS_STAC,
674 UC_X86_INS_STC,
675 UC_X86_INS_STD,
676 UC_X86_INS_STGI,
677 UC_X86_INS_STI,
678 UC_X86_INS_STMXCSR,
679 UC_X86_INS_STOSB,
680 UC_X86_INS_STOSD,
681 UC_X86_INS_STOSQ,
682 UC_X86_INS_STOSW,
683 UC_X86_INS_STR,
684 UC_X86_INS_FST,
685 UC_X86_INS_FSTP,
686 UC_X86_INS_FSTPNCE,
687 UC_X86_INS_FXCH,
688 UC_X86_INS_SUBPD,
689 UC_X86_INS_SUBPS,
690 UC_X86_INS_FSUBR,
691 UC_X86_INS_FISUBR,
692 UC_X86_INS_FSUBRP,
693 UC_X86_INS_SUBSD,
694 UC_X86_INS_SUBSS,
695 UC_X86_INS_FSUB,
696 UC_X86_INS_FISUB,
697 UC_X86_INS_FSUBP,
698 UC_X86_INS_SWAPGS,
699 UC_X86_INS_SYSCALL,
700 UC_X86_INS_SYSENTER,
701 UC_X86_INS_SYSEXIT,
702 UC_X86_INS_SYSRET,
703 UC_X86_INS_T1MSKC,
704 UC_X86_INS_TEST,
705 UC_X86_INS_UD2,
706 UC_X86_INS_FTST,
707 UC_X86_INS_TZCNT,
708 UC_X86_INS_TZMSK,
709 UC_X86_INS_FUCOMPI,
710 UC_X86_INS_FUCOMI,
711 UC_X86_INS_FUCOMPP,
712 UC_X86_INS_FUCOMP,
713 UC_X86_INS_FUCOM,
714 UC_X86_INS_UD2B,
715 UC_X86_INS_UNPCKHPD,
716 UC_X86_INS_UNPCKHPS,
717 UC_X86_INS_UNPCKLPD,
718 UC_X86_INS_UNPCKLPS,
719 UC_X86_INS_VADDPD,
720 UC_X86_INS_VADDPS,
721 UC_X86_INS_VADDSD,
722 UC_X86_INS_VADDSS,
723 UC_X86_INS_VADDSUBPD,
724 UC_X86_INS_VADDSUBPS,
725 UC_X86_INS_VAESDECLAST,
726 UC_X86_INS_VAESDEC,
727 UC_X86_INS_VAESENCLAST,
728 UC_X86_INS_VAESENC,
729 UC_X86_INS_VAESIMC,
730 UC_X86_INS_VAESKEYGENASSIST,
731 UC_X86_INS_VALIGND,
732 UC_X86_INS_VALIGNQ,
733 UC_X86_INS_VANDNPD,
734 UC_X86_INS_VANDNPS,
735 UC_X86_INS_VANDPD,
736 UC_X86_INS_VANDPS,
737 UC_X86_INS_VBLENDMPD,
738 UC_X86_INS_VBLENDMPS,
739 UC_X86_INS_VBLENDPD,
740 UC_X86_INS_VBLENDPS,
741 UC_X86_INS_VBLENDVPD,
742 UC_X86_INS_VBLENDVPS,
743 UC_X86_INS_VBROADCASTF128,
744 UC_X86_INS_VBROADCASTI32X4,
745 UC_X86_INS_VBROADCASTI64X4,
746 UC_X86_INS_VBROADCASTSD,
747 UC_X86_INS_VBROADCASTSS,
748 UC_X86_INS_VCMPPD,
749 UC_X86_INS_VCMPPS,
750 UC_X86_INS_VCMPSD,
751 UC_X86_INS_VCMPSS,
752 UC_X86_INS_VCOMPRESSPD,
753 UC_X86_INS_VCOMPRESSPS,
754 UC_X86_INS_VCVTDQ2PD,
755 UC_X86_INS_VCVTDQ2PS,
756 UC_X86_INS_VCVTPD2DQX,
757 UC_X86_INS_VCVTPD2DQ,
758 UC_X86_INS_VCVTPD2PSX,
759 UC_X86_INS_VCVTPD2PS,
760 UC_X86_INS_VCVTPD2UDQ,
761 UC_X86_INS_VCVTPH2PS,
762 UC_X86_INS_VCVTPS2DQ,
763 UC_X86_INS_VCVTPS2PD,
764 UC_X86_INS_VCVTPS2PH,
765 UC_X86_INS_VCVTPS2UDQ,
766 UC_X86_INS_VCVTSD2SI,
767 UC_X86_INS_VCVTSD2USI,
768 UC_X86_INS_VCVTSS2SI,
769 UC_X86_INS_VCVTSS2USI,
770 UC_X86_INS_VCVTTPD2DQX,
771 UC_X86_INS_VCVTTPD2DQ,
772 UC_X86_INS_VCVTTPD2UDQ,
773 UC_X86_INS_VCVTTPS2DQ,
774 UC_X86_INS_VCVTTPS2UDQ,
775 UC_X86_INS_VCVTUDQ2PD,
776 UC_X86_INS_VCVTUDQ2PS,
777 UC_X86_INS_VDIVPD,
778 UC_X86_INS_VDIVPS,
779 UC_X86_INS_VDIVSD,
780 UC_X86_INS_VDIVSS,
781 UC_X86_INS_VDPPD,
782 UC_X86_INS_VDPPS,
783 UC_X86_INS_VERR,
784 UC_X86_INS_VERW,
785 UC_X86_INS_VEXP2PD,
786 UC_X86_INS_VEXP2PS,
787 UC_X86_INS_VEXPANDPD,
788 UC_X86_INS_VEXPANDPS,
789 UC_X86_INS_VEXTRACTF128,
790 UC_X86_INS_VEXTRACTF32X4,
791 UC_X86_INS_VEXTRACTF64X4,
792 UC_X86_INS_VEXTRACTI128,
793 UC_X86_INS_VEXTRACTI32X4,
794 UC_X86_INS_VEXTRACTI64X4,
795 UC_X86_INS_VEXTRACTPS,
796 UC_X86_INS_VFMADD132PD,
797 UC_X86_INS_VFMADD132PS,
798 UC_X86_INS_VFMADDPD,
799 UC_X86_INS_VFMADD213PD,
800 UC_X86_INS_VFMADD231PD,
801 UC_X86_INS_VFMADDPS,
802 UC_X86_INS_VFMADD213PS,
803 UC_X86_INS_VFMADD231PS,
804 UC_X86_INS_VFMADDSD,
805 UC_X86_INS_VFMADD213SD,
806 UC_X86_INS_VFMADD132SD,
807 UC_X86_INS_VFMADD231SD,
808 UC_X86_INS_VFMADDSS,
809 UC_X86_INS_VFMADD213SS,
810 UC_X86_INS_VFMADD132SS,
811 UC_X86_INS_VFMADD231SS,
812 UC_X86_INS_VFMADDSUB132PD,
813 UC_X86_INS_VFMADDSUB132PS,
814 UC_X86_INS_VFMADDSUBPD,
815 UC_X86_INS_VFMADDSUB213PD,
816 UC_X86_INS_VFMADDSUB231PD,
817 UC_X86_INS_VFMADDSUBPS,
818 UC_X86_INS_VFMADDSUB213PS,
819 UC_X86_INS_VFMADDSUB231PS,
820 UC_X86_INS_VFMSUB132PD,
821 UC_X86_INS_VFMSUB132PS,
822 UC_X86_INS_VFMSUBADD132PD,
823 UC_X86_INS_VFMSUBADD132PS,
824 UC_X86_INS_VFMSUBADDPD,
825 UC_X86_INS_VFMSUBADD213PD,
826 UC_X86_INS_VFMSUBADD231PD,
827 UC_X86_INS_VFMSUBADDPS,
828 UC_X86_INS_VFMSUBADD213PS,
829 UC_X86_INS_VFMSUBADD231PS,
830 UC_X86_INS_VFMSUBPD,
831 UC_X86_INS_VFMSUB213PD,
832 UC_X86_INS_VFMSUB231PD,
833 UC_X86_INS_VFMSUBPS,
834 UC_X86_INS_VFMSUB213PS,
835 UC_X86_INS_VFMSUB231PS,
836 UC_X86_INS_VFMSUBSD,
837 UC_X86_INS_VFMSUB213SD,
838 UC_X86_INS_VFMSUB132SD,
839 UC_X86_INS_VFMSUB231SD,
840 UC_X86_INS_VFMSUBSS,
841 UC_X86_INS_VFMSUB213SS,
842 UC_X86_INS_VFMSUB132SS,
843 UC_X86_INS_VFMSUB231SS,
844 UC_X86_INS_VFNMADD132PD,
845 UC_X86_INS_VFNMADD132PS,
846 UC_X86_INS_VFNMADDPD,
847 UC_X86_INS_VFNMADD213PD,
848 UC_X86_INS_VFNMADD231PD,
849 UC_X86_INS_VFNMADDPS,
850 UC_X86_INS_VFNMADD213PS,
851 UC_X86_INS_VFNMADD231PS,
852 UC_X86_INS_VFNMADDSD,
853 UC_X86_INS_VFNMADD213SD,
854 UC_X86_INS_VFNMADD132SD,
855 UC_X86_INS_VFNMADD231SD,
856 UC_X86_INS_VFNMADDSS,
857 UC_X86_INS_VFNMADD213SS,
858 UC_X86_INS_VFNMADD132SS,
859 UC_X86_INS_VFNMADD231SS,
860 UC_X86_INS_VFNMSUB132PD,
861 UC_X86_INS_VFNMSUB132PS,
862 UC_X86_INS_VFNMSUBPD,
863 UC_X86_INS_VFNMSUB213PD,
864 UC_X86_INS_VFNMSUB231PD,
865 UC_X86_INS_VFNMSUBPS,
866 UC_X86_INS_VFNMSUB213PS,
867 UC_X86_INS_VFNMSUB231PS,
868 UC_X86_INS_VFNMSUBSD,
869 UC_X86_INS_VFNMSUB213SD,
870 UC_X86_INS_VFNMSUB132SD,
871 UC_X86_INS_VFNMSUB231SD,
872 UC_X86_INS_VFNMSUBSS,
873 UC_X86_INS_VFNMSUB213SS,
874 UC_X86_INS_VFNMSUB132SS,
875 UC_X86_INS_VFNMSUB231SS,
876 UC_X86_INS_VFRCZPD,
877 UC_X86_INS_VFRCZPS,
878 UC_X86_INS_VFRCZSD,
879 UC_X86_INS_VFRCZSS,
880 UC_X86_INS_VORPD,
881 UC_X86_INS_VORPS,
882 UC_X86_INS_VXORPD,
883 UC_X86_INS_VXORPS,
884 UC_X86_INS_VGATHERDPD,
885 UC_X86_INS_VGATHERDPS,
886 UC_X86_INS_VGATHERPF0DPD,
887 UC_X86_INS_VGATHERPF0DPS,
888 UC_X86_INS_VGATHERPF0QPD,
889 UC_X86_INS_VGATHERPF0QPS,
890 UC_X86_INS_VGATHERPF1DPD,
891 UC_X86_INS_VGATHERPF1DPS,
892 UC_X86_INS_VGATHERPF1QPD,
893 UC_X86_INS_VGATHERPF1QPS,
894 UC_X86_INS_VGATHERQPD,
895 UC_X86_INS_VGATHERQPS,
896 UC_X86_INS_VHADDPD,
897 UC_X86_INS_VHADDPS,
898 UC_X86_INS_VHSUBPD,
899 UC_X86_INS_VHSUBPS,
900 UC_X86_INS_VINSERTF128,
901 UC_X86_INS_VINSERTF32X4,
902 UC_X86_INS_VINSERTF32X8,
903 UC_X86_INS_VINSERTF64X2,
904 UC_X86_INS_VINSERTF64X4,
905 UC_X86_INS_VINSERTI128,
906 UC_X86_INS_VINSERTI32X4,
907 UC_X86_INS_VINSERTI32X8,
908 UC_X86_INS_VINSERTI64X2,
909 UC_X86_INS_VINSERTI64X4,
910 UC_X86_INS_VINSERTPS,
911 UC_X86_INS_VLDDQU,
912 UC_X86_INS_VLDMXCSR,
913 UC_X86_INS_VMASKMOVDQU,
914 UC_X86_INS_VMASKMOVPD,
915 UC_X86_INS_VMASKMOVPS,
916 UC_X86_INS_VMAXPD,
917 UC_X86_INS_VMAXPS,
918 UC_X86_INS_VMAXSD,
919 UC_X86_INS_VMAXSS,
920 UC_X86_INS_VMCALL,
921 UC_X86_INS_VMCLEAR,
922 UC_X86_INS_VMFUNC,
923 UC_X86_INS_VMINPD,
924 UC_X86_INS_VMINPS,
925 UC_X86_INS_VMINSD,
926 UC_X86_INS_VMINSS,
927 UC_X86_INS_VMLAUNCH,
928 UC_X86_INS_VMLOAD,
929 UC_X86_INS_VMMCALL,
930 UC_X86_INS_VMOVQ,
931 UC_X86_INS_VMOVDDUP,
932 UC_X86_INS_VMOVD,
933 UC_X86_INS_VMOVDQA32,
934 UC_X86_INS_VMOVDQA64,
935 UC_X86_INS_VMOVDQA,
936 UC_X86_INS_VMOVDQU16,
937 UC_X86_INS_VMOVDQU32,
938 UC_X86_INS_VMOVDQU64,
939 UC_X86_INS_VMOVDQU8,
940 UC_X86_INS_VMOVDQU,
941 UC_X86_INS_VMOVHLPS,
942 UC_X86_INS_VMOVHPD,
943 UC_X86_INS_VMOVHPS,
944 UC_X86_INS_VMOVLHPS,
945 UC_X86_INS_VMOVLPD,
946 UC_X86_INS_VMOVLPS,
947 UC_X86_INS_VMOVMSKPD,
948 UC_X86_INS_VMOVMSKPS,
949 UC_X86_INS_VMOVNTDQA,
950 UC_X86_INS_VMOVNTDQ,
951 UC_X86_INS_VMOVNTPD,
952 UC_X86_INS_VMOVNTPS,
953 UC_X86_INS_VMOVSD,
954 UC_X86_INS_VMOVSHDUP,
955 UC_X86_INS_VMOVSLDUP,
956 UC_X86_INS_VMOVSS,
957 UC_X86_INS_VMOVUPD,
958 UC_X86_INS_VMOVUPS,
959 UC_X86_INS_VMPSADBW,
960 UC_X86_INS_VMPTRLD,
961 UC_X86_INS_VMPTRST,
962 UC_X86_INS_VMREAD,
963 UC_X86_INS_VMRESUME,
964 UC_X86_INS_VMRUN,
965 UC_X86_INS_VMSAVE,
966 UC_X86_INS_VMULPD,
967 UC_X86_INS_VMULPS,
968 UC_X86_INS_VMULSD,
969 UC_X86_INS_VMULSS,
970 UC_X86_INS_VMWRITE,
971 UC_X86_INS_VMXOFF,
972 UC_X86_INS_VMXON,
973 UC_X86_INS_VPABSB,
974 UC_X86_INS_VPABSD,
975 UC_X86_INS_VPABSQ,
976 UC_X86_INS_VPABSW,
977 UC_X86_INS_VPACKSSDW,
978 UC_X86_INS_VPACKSSWB,
979 UC_X86_INS_VPACKUSDW,
980 UC_X86_INS_VPACKUSWB,
981 UC_X86_INS_VPADDB,
982 UC_X86_INS_VPADDD,
983 UC_X86_INS_VPADDQ,
984 UC_X86_INS_VPADDSB,
985 UC_X86_INS_VPADDSW,
986 UC_X86_INS_VPADDUSB,
987 UC_X86_INS_VPADDUSW,
988 UC_X86_INS_VPADDW,
989 UC_X86_INS_VPALIGNR,
990 UC_X86_INS_VPANDD,
991 UC_X86_INS_VPANDND,
992 UC_X86_INS_VPANDNQ,
993 UC_X86_INS_VPANDN,
994 UC_X86_INS_VPANDQ,
995 UC_X86_INS_VPAND,
996 UC_X86_INS_VPAVGB,
997 UC_X86_INS_VPAVGW,
998 UC_X86_INS_VPBLENDD,
999 UC_X86_INS_VPBLENDMB,
1000 UC_X86_INS_VPBLENDMD,
1001 UC_X86_INS_VPBLENDMQ,
1002 UC_X86_INS_VPBLENDMW,
1003 UC_X86_INS_VPBLENDVB,
1004 UC_X86_INS_VPBLENDW,
1005 UC_X86_INS_VPBROADCASTB,
1006 UC_X86_INS_VPBROADCASTD,
1007 UC_X86_INS_VPBROADCASTMB2Q,
1008 UC_X86_INS_VPBROADCASTMW2D,
1009 UC_X86_INS_VPBROADCASTQ,
1010 UC_X86_INS_VPBROADCASTW,
1011 UC_X86_INS_VPCLMULQDQ,
1012 UC_X86_INS_VPCMOV,
1013 UC_X86_INS_VPCMPB,
1014 UC_X86_INS_VPCMPD,
1015 UC_X86_INS_VPCMPEQB,
1016 UC_X86_INS_VPCMPEQD,
1017 UC_X86_INS_VPCMPEQQ,
1018 UC_X86_INS_VPCMPEQW,
1019 UC_X86_INS_VPCMPESTRI,
1020 UC_X86_INS_VPCMPESTRM,
1021 UC_X86_INS_VPCMPGTB,
1022 UC_X86_INS_VPCMPGTD,
1023 UC_X86_INS_VPCMPGTQ,
1024 UC_X86_INS_VPCMPGTW,
1025 UC_X86_INS_VPCMPISTRI,
1026 UC_X86_INS_VPCMPISTRM,
1027 UC_X86_INS_VPCMPQ,
1028 UC_X86_INS_VPCMPUB,
1029 UC_X86_INS_VPCMPUD,
1030 UC_X86_INS_VPCMPUQ,
1031 UC_X86_INS_VPCMPUW,
1032 UC_X86_INS_VPCMPW,
1033 UC_X86_INS_VPCOMB,
1034 UC_X86_INS_VPCOMD,
1035 UC_X86_INS_VPCOMPRESSD,
1036 UC_X86_INS_VPCOMPRESSQ,
1037 UC_X86_INS_VPCOMQ,
1038 UC_X86_INS_VPCOMUB,
1039 UC_X86_INS_VPCOMUD,
1040 UC_X86_INS_VPCOMUQ,
1041 UC_X86_INS_VPCOMUW,
1042 UC_X86_INS_VPCOMW,
1043 UC_X86_INS_VPCONFLICTD,
1044 UC_X86_INS_VPCONFLICTQ,
1045 UC_X86_INS_VPERM2F128,
1046 UC_X86_INS_VPERM2I128,
1047 UC_X86_INS_VPERMD,
1048 UC_X86_INS_VPERMI2D,
1049 UC_X86_INS_VPERMI2PD,
1050 UC_X86_INS_VPERMI2PS,
1051 UC_X86_INS_VPERMI2Q,
1052 UC_X86_INS_VPERMIL2PD,
1053 UC_X86_INS_VPERMIL2PS,
1054 UC_X86_INS_VPERMILPD,
1055 UC_X86_INS_VPERMILPS,
1056 UC_X86_INS_VPERMPD,
1057 UC_X86_INS_VPERMPS,
1058 UC_X86_INS_VPERMQ,
1059 UC_X86_INS_VPERMT2D,
1060 UC_X86_INS_VPERMT2PD,
1061 UC_X86_INS_VPERMT2PS,
1062 UC_X86_INS_VPERMT2Q,
1063 UC_X86_INS_VPEXPANDD,
1064 UC_X86_INS_VPEXPANDQ,
1065 UC_X86_INS_VPEXTRB,
1066 UC_X86_INS_VPEXTRD,
1067 UC_X86_INS_VPEXTRQ,
1068 UC_X86_INS_VPEXTRW,
1069 UC_X86_INS_VPGATHERDD,
1070 UC_X86_INS_VPGATHERDQ,
1071 UC_X86_INS_VPGATHERQD,
1072 UC_X86_INS_VPGATHERQQ,
1073 UC_X86_INS_VPHADDBD,
1074 UC_X86_INS_VPHADDBQ,
1075 UC_X86_INS_VPHADDBW,
1076 UC_X86_INS_VPHADDDQ,
1077 UC_X86_INS_VPHADDD,
1078 UC_X86_INS_VPHADDSW,
1079 UC_X86_INS_VPHADDUBD,
1080 UC_X86_INS_VPHADDUBQ,
1081 UC_X86_INS_VPHADDUBW,
1082 UC_X86_INS_VPHADDUDQ,
1083 UC_X86_INS_VPHADDUWD,
1084 UC_X86_INS_VPHADDUWQ,
1085 UC_X86_INS_VPHADDWD,
1086 UC_X86_INS_VPHADDWQ,
1087 UC_X86_INS_VPHADDW,
1088 UC_X86_INS_VPHMINPOSUW,
1089 UC_X86_INS_VPHSUBBW,
1090 UC_X86_INS_VPHSUBDQ,
1091 UC_X86_INS_VPHSUBD,
1092 UC_X86_INS_VPHSUBSW,
1093 UC_X86_INS_VPHSUBWD,
1094 UC_X86_INS_VPHSUBW,
1095 UC_X86_INS_VPINSRB,
1096 UC_X86_INS_VPINSRD,
1097 UC_X86_INS_VPINSRQ,
1098 UC_X86_INS_VPINSRW,
1099 UC_X86_INS_VPLZCNTD,
1100 UC_X86_INS_VPLZCNTQ,
1101 UC_X86_INS_VPMACSDD,
1102 UC_X86_INS_VPMACSDQH,
1103 UC_X86_INS_VPMACSDQL,
1104 UC_X86_INS_VPMACSSDD,
1105 UC_X86_INS_VPMACSSDQH,
1106 UC_X86_INS_VPMACSSDQL,
1107 UC_X86_INS_VPMACSSWD,
1108 UC_X86_INS_VPMACSSWW,
1109 UC_X86_INS_VPMACSWD,
1110 UC_X86_INS_VPMACSWW,
1111 UC_X86_INS_VPMADCSSWD,
1112 UC_X86_INS_VPMADCSWD,
1113 UC_X86_INS_VPMADDUBSW,
1114 UC_X86_INS_VPMADDWD,
1115 UC_X86_INS_VPMASKMOVD,
1116 UC_X86_INS_VPMASKMOVQ,
1117 UC_X86_INS_VPMAXSB,
1118 UC_X86_INS_VPMAXSD,
1119 UC_X86_INS_VPMAXSQ,
1120 UC_X86_INS_VPMAXSW,
1121 UC_X86_INS_VPMAXUB,
1122 UC_X86_INS_VPMAXUD,
1123 UC_X86_INS_VPMAXUQ,
1124 UC_X86_INS_VPMAXUW,
1125 UC_X86_INS_VPMINSB,
1126 UC_X86_INS_VPMINSD,
1127 UC_X86_INS_VPMINSQ,
1128 UC_X86_INS_VPMINSW,
1129 UC_X86_INS_VPMINUB,
1130 UC_X86_INS_VPMINUD,
1131 UC_X86_INS_VPMINUQ,
1132 UC_X86_INS_VPMINUW,
1133 UC_X86_INS_VPMOVDB,
1134 UC_X86_INS_VPMOVDW,
1135 UC_X86_INS_VPMOVM2B,
1136 UC_X86_INS_VPMOVM2D,
1137 UC_X86_INS_VPMOVM2Q,
1138 UC_X86_INS_VPMOVM2W,
1139 UC_X86_INS_VPMOVMSKB,
1140 UC_X86_INS_VPMOVQB,
1141 UC_X86_INS_VPMOVQD,
1142 UC_X86_INS_VPMOVQW,
1143 UC_X86_INS_VPMOVSDB,
1144 UC_X86_INS_VPMOVSDW,
1145 UC_X86_INS_VPMOVSQB,
1146 UC_X86_INS_VPMOVSQD,
1147 UC_X86_INS_VPMOVSQW,
1148 UC_X86_INS_VPMOVSXBD,
1149 UC_X86_INS_VPMOVSXBQ,
1150 UC_X86_INS_VPMOVSXBW,
1151 UC_X86_INS_VPMOVSXDQ,
1152 UC_X86_INS_VPMOVSXWD,
1153 UC_X86_INS_VPMOVSXWQ,
1154 UC_X86_INS_VPMOVUSDB,
1155 UC_X86_INS_VPMOVUSDW,
1156 UC_X86_INS_VPMOVUSQB,
1157 UC_X86_INS_VPMOVUSQD,
1158 UC_X86_INS_VPMOVUSQW,
1159 UC_X86_INS_VPMOVZXBD,
1160 UC_X86_INS_VPMOVZXBQ,
1161 UC_X86_INS_VPMOVZXBW,
1162 UC_X86_INS_VPMOVZXDQ,
1163 UC_X86_INS_VPMOVZXWD,
1164 UC_X86_INS_VPMOVZXWQ,
1165 UC_X86_INS_VPMULDQ,
1166 UC_X86_INS_VPMULHRSW,
1167 UC_X86_INS_VPMULHUW,
1168 UC_X86_INS_VPMULHW,
1169 UC_X86_INS_VPMULLD,
1170 UC_X86_INS_VPMULLQ,
1171 UC_X86_INS_VPMULLW,
1172 UC_X86_INS_VPMULUDQ,
1173 UC_X86_INS_VPORD,
1174 UC_X86_INS_VPORQ,
1175 UC_X86_INS_VPOR,
1176 UC_X86_INS_VPPERM,
1177 UC_X86_INS_VPROTB,
1178 UC_X86_INS_VPROTD,
1179 UC_X86_INS_VPROTQ,
1180 UC_X86_INS_VPROTW,
1181 UC_X86_INS_VPSADBW,
1182 UC_X86_INS_VPSCATTERDD,
1183 UC_X86_INS_VPSCATTERDQ,
1184 UC_X86_INS_VPSCATTERQD,
1185 UC_X86_INS_VPSCATTERQQ,
1186 UC_X86_INS_VPSHAB,
1187 UC_X86_INS_VPSHAD,
1188 UC_X86_INS_VPSHAQ,
1189 UC_X86_INS_VPSHAW,
1190 UC_X86_INS_VPSHLB,
1191 UC_X86_INS_VPSHLD,
1192 UC_X86_INS_VPSHLQ,
1193 UC_X86_INS_VPSHLW,
1194 UC_X86_INS_VPSHUFB,
1195 UC_X86_INS_VPSHUFD,
1196 UC_X86_INS_VPSHUFHW,
1197 UC_X86_INS_VPSHUFLW,
1198 UC_X86_INS_VPSIGNB,
1199 UC_X86_INS_VPSIGND,
1200 UC_X86_INS_VPSIGNW,
1201 UC_X86_INS_VPSLLDQ,
1202 UC_X86_INS_VPSLLD,
1203 UC_X86_INS_VPSLLQ,
1204 UC_X86_INS_VPSLLVD,
1205 UC_X86_INS_VPSLLVQ,
1206 UC_X86_INS_VPSLLW,
1207 UC_X86_INS_VPSRAD,
1208 UC_X86_INS_VPSRAQ,
1209 UC_X86_INS_VPSRAVD,
1210 UC_X86_INS_VPSRAVQ,
1211 UC_X86_INS_VPSRAW,
1212 UC_X86_INS_VPSRLDQ,
1213 UC_X86_INS_VPSRLD,
1214 UC_X86_INS_VPSRLQ,
1215 UC_X86_INS_VPSRLVD,
1216 UC_X86_INS_VPSRLVQ,
1217 UC_X86_INS_VPSRLW,
1218 UC_X86_INS_VPSUBB,
1219 UC_X86_INS_VPSUBD,
1220 UC_X86_INS_VPSUBQ,
1221 UC_X86_INS_VPSUBSB,
1222 UC_X86_INS_VPSUBSW,
1223 UC_X86_INS_VPSUBUSB,
1224 UC_X86_INS_VPSUBUSW,
1225 UC_X86_INS_VPSUBW,
1226 UC_X86_INS_VPTESTMD,
1227 UC_X86_INS_VPTESTMQ,
1228 UC_X86_INS_VPTESTNMD,
1229 UC_X86_INS_VPTESTNMQ,
1230 UC_X86_INS_VPTEST,
1231 UC_X86_INS_VPUNPCKHBW,
1232 UC_X86_INS_VPUNPCKHDQ,
1233 UC_X86_INS_VPUNPCKHQDQ,
1234 UC_X86_INS_VPUNPCKHWD,
1235 UC_X86_INS_VPUNPCKLBW,
1236 UC_X86_INS_VPUNPCKLDQ,
1237 UC_X86_INS_VPUNPCKLQDQ,
1238 UC_X86_INS_VPUNPCKLWD,
1239 UC_X86_INS_VPXORD,
1240 UC_X86_INS_VPXORQ,
1241 UC_X86_INS_VPXOR,
1242 UC_X86_INS_VRCP14PD,
1243 UC_X86_INS_VRCP14PS,
1244 UC_X86_INS_VRCP14SD,
1245 UC_X86_INS_VRCP14SS,
1246 UC_X86_INS_VRCP28PD,
1247 UC_X86_INS_VRCP28PS,
1248 UC_X86_INS_VRCP28SD,
1249 UC_X86_INS_VRCP28SS,
1250 UC_X86_INS_VRCPPS,
1251 UC_X86_INS_VRCPSS,
1252 UC_X86_INS_VRNDSCALEPD,
1253 UC_X86_INS_VRNDSCALEPS,
1254 UC_X86_INS_VRNDSCALESD,
1255 UC_X86_INS_VRNDSCALESS,
1256 UC_X86_INS_VROUNDPD,
1257 UC_X86_INS_VROUNDPS,
1258 UC_X86_INS_VROUNDSD,
1259 UC_X86_INS_VROUNDSS,
1260 UC_X86_INS_VRSQRT14PD,
1261 UC_X86_INS_VRSQRT14PS,
1262 UC_X86_INS_VRSQRT14SD,
1263 UC_X86_INS_VRSQRT14SS,
1264 UC_X86_INS_VRSQRT28PD,
1265 UC_X86_INS_VRSQRT28PS,
1266 UC_X86_INS_VRSQRT28SD,
1267 UC_X86_INS_VRSQRT28SS,
1268 UC_X86_INS_VRSQRTPS,
1269 UC_X86_INS_VRSQRTSS,
1270 UC_X86_INS_VSCATTERDPD,
1271 UC_X86_INS_VSCATTERDPS,
1272 UC_X86_INS_VSCATTERPF0DPD,
1273 UC_X86_INS_VSCATTERPF0DPS,
1274 UC_X86_INS_VSCATTERPF0QPD,
1275 UC_X86_INS_VSCATTERPF0QPS,
1276 UC_X86_INS_VSCATTERPF1DPD,
1277 UC_X86_INS_VSCATTERPF1DPS,
1278 UC_X86_INS_VSCATTERPF1QPD,
1279 UC_X86_INS_VSCATTERPF1QPS,
1280 UC_X86_INS_VSCATTERQPD,
1281 UC_X86_INS_VSCATTERQPS,
1282 UC_X86_INS_VSHUFPD,
1283 UC_X86_INS_VSHUFPS,
1284 UC_X86_INS_VSQRTPD,
1285 UC_X86_INS_VSQRTPS,
1286 UC_X86_INS_VSQRTSD,
1287 UC_X86_INS_VSQRTSS,
1288 UC_X86_INS_VSTMXCSR,
1289 UC_X86_INS_VSUBPD,
1290 UC_X86_INS_VSUBPS,
1291 UC_X86_INS_VSUBSD,
1292 UC_X86_INS_VSUBSS,
1293 UC_X86_INS_VTESTPD,
1294 UC_X86_INS_VTESTPS,
1295 UC_X86_INS_VUNPCKHPD,
1296 UC_X86_INS_VUNPCKHPS,
1297 UC_X86_INS_VUNPCKLPD,
1298 UC_X86_INS_VUNPCKLPS,
1299 UC_X86_INS_VZEROALL,
1300 UC_X86_INS_VZEROUPPER,
1301 UC_X86_INS_WAIT,
1302 UC_X86_INS_WBINVD,
1303 UC_X86_INS_WRFSBASE,
1304 UC_X86_INS_WRGSBASE,
1305 UC_X86_INS_WRMSR,
1306 UC_X86_INS_XABORT,
1307 UC_X86_INS_XACQUIRE,
1308 UC_X86_INS_XBEGIN,
1309 UC_X86_INS_XCHG,
1310 UC_X86_INS_XCRYPTCBC,
1311 UC_X86_INS_XCRYPTCFB,
1312 UC_X86_INS_XCRYPTCTR,
1313 UC_X86_INS_XCRYPTECB,
1314 UC_X86_INS_XCRYPTOFB,
1315 UC_X86_INS_XEND,
1316 UC_X86_INS_XGETBV,
1317 UC_X86_INS_XLATB,
1318 UC_X86_INS_XRELEASE,
1319 UC_X86_INS_XRSTOR,
1320 UC_X86_INS_XRSTOR64,
1321 UC_X86_INS_XRSTORS,
1322 UC_X86_INS_XRSTORS64,
1323 UC_X86_INS_XSAVE,
1324 UC_X86_INS_XSAVE64,
1325 UC_X86_INS_XSAVEC,
1326 UC_X86_INS_XSAVEC64,
1327 UC_X86_INS_XSAVEOPT,
1328 UC_X86_INS_XSAVEOPT64,
1329 UC_X86_INS_XSAVES,
1330 UC_X86_INS_XSAVES64,
1331 UC_X86_INS_XSETBV,
1332 UC_X86_INS_XSHA1,
1333 UC_X86_INS_XSHA256,
1334 UC_X86_INS_XSTORE,
1335 UC_X86_INS_XTEST,
1336 UC_X86_INS_FDISI8087_NOP,
1337 UC_X86_INS_FENI8087_NOP,
1338 UC_X86_INS_ENDING,
} uc_x86_insn;
|