NUCTF-部分wp
本文最后更新于:2021年6月9日 下午
Reverse
encryption
程序有自加密代码,直接动态调试得到解密的代码。
根据特征发现是rc4加密,找到key和最终比较的结果,解密即可。
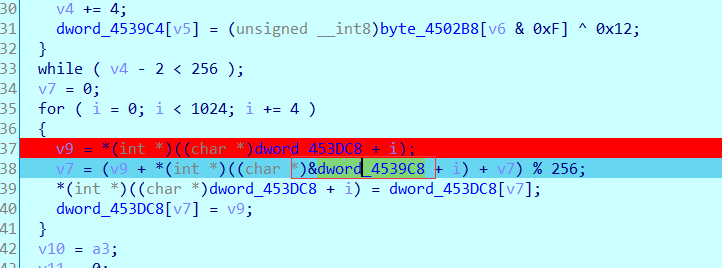
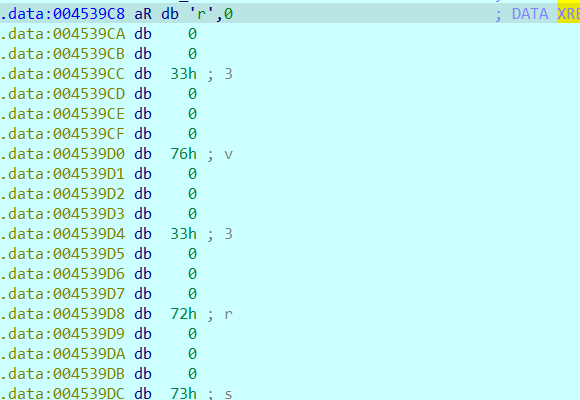
得到key:r3v3rs3_1s_s0_3z
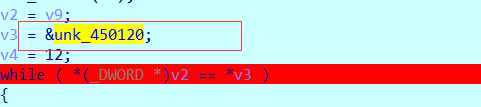
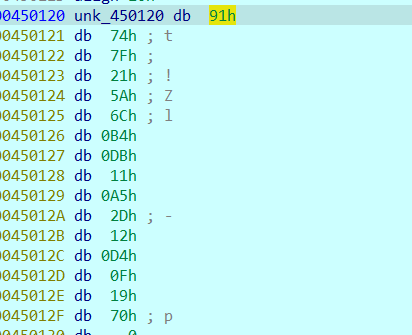
最终比较的结果:91747F215A6CB4DB11A52D12D40F1970
进行解密:
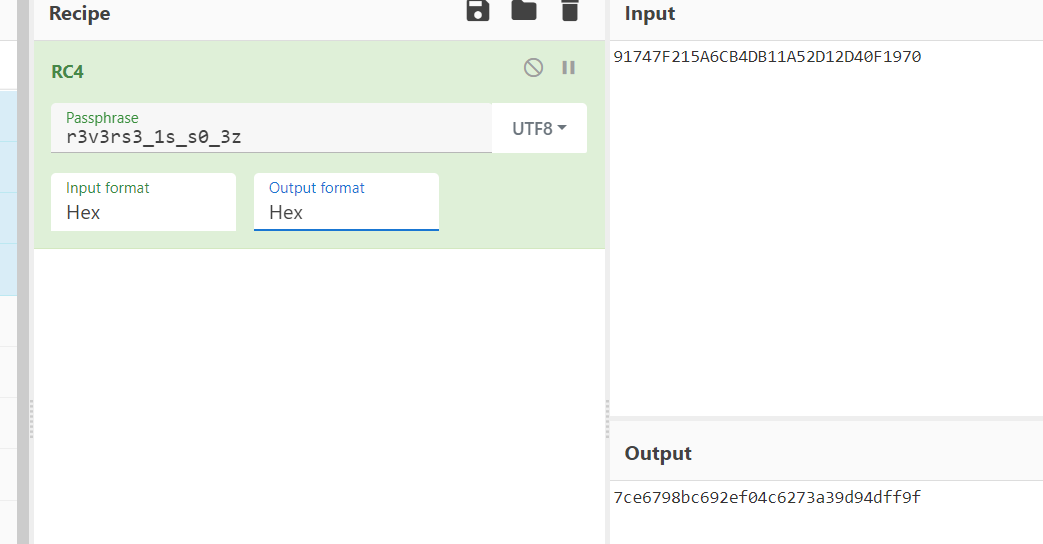
flag为:DACTF{7ce6798bc692ef04c6273a39d94dff9f}
vmm
给了opcode,所以去找opcode所对应的指令函数即可。
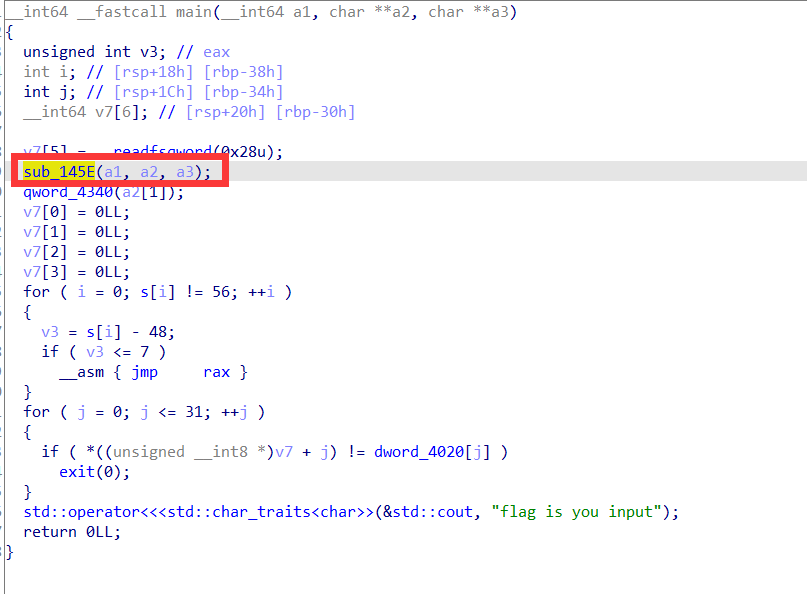
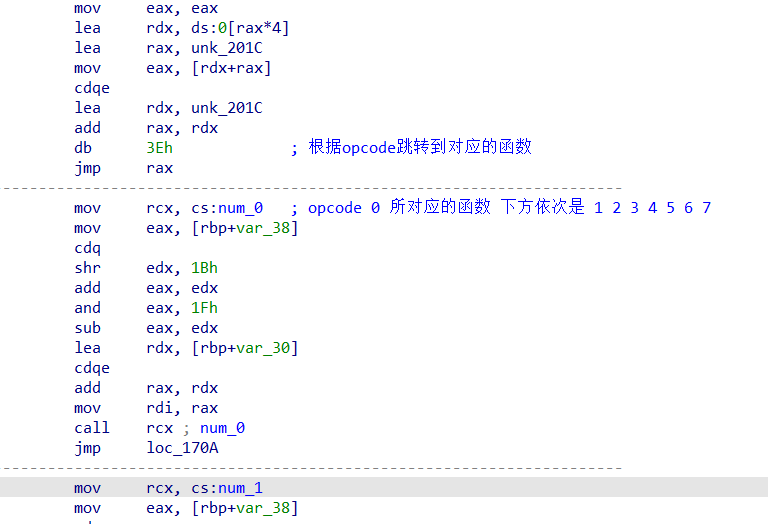
修改完函数名再回到第一张图里的函数,
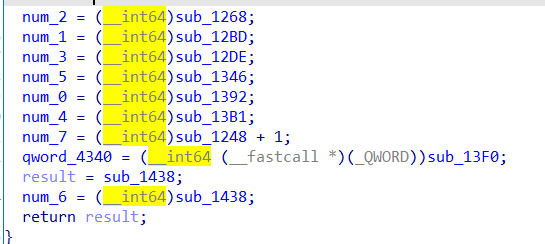
然后去分析这些函数。
这里要注意num_5这个函数:
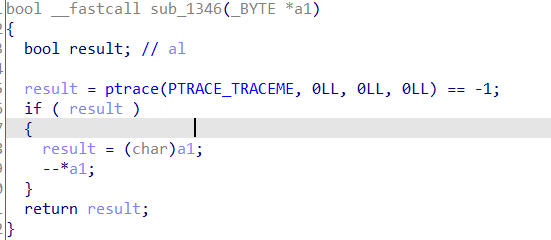
如果在调试,则会执行减1运算。
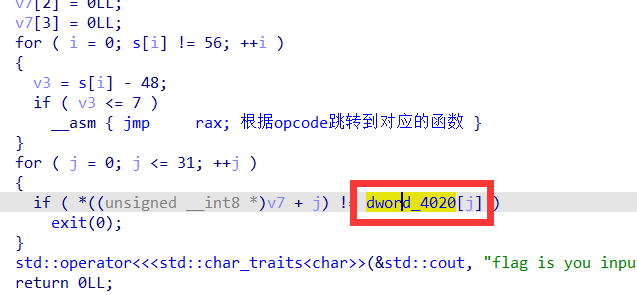
最后得出opcode指令:
1 | |
得到最后比较的结果:
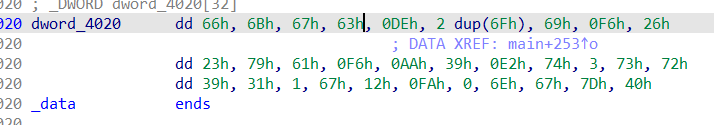
写python脚本进行还原:
1 | |
flag为:flag{goood!_yoU_Gett_r1ght_fl@g}
anbug
没有符号表,直接动态调试。
关键地方做了注释:
1 | |
python脚本解密:
1 | |
flag为:DASCTF{Mut1Thre4d_Ant1_D3bu8_14Easy}
MISC
艾斯的信仰
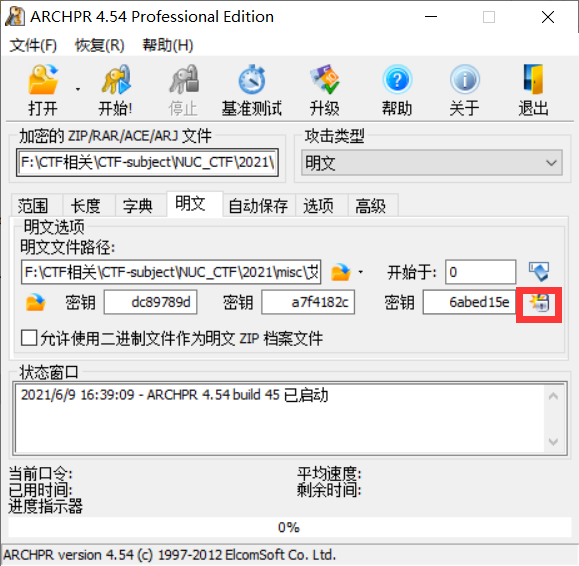
压缩包 明文攻击。
跑出密钥进行解密:
打开flag.txt 发现当铺密码,解密即可。
yusa的音乐
010打开,将00替换为0x30,将0xff替换为0x31,然后粘贴二进制文本,得到rar文件。
得到一个hint和一个png图片。
hint是零宽字符隐写。
进行解密:https://stylesuxx.github.io/steganography/
flag_is:91ec477ed0cccb2f5d6393cc2880f273
funnygame
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!