虎符2022逆向部分wp
本文最后更新于:2022年3月28日 晚上
reverse
2048
加载webview,一个2048游戏。MainActivity中点击十次进入TestActivity,但是点击后无效,猜测可能隐藏按钮,不知道在哪个地方,也不需要分析layout文件,直接使用命令adb shell am start -n com.test.hufu22/.TestActivity即可进入游戏界面。TestActivity中有JS接口,
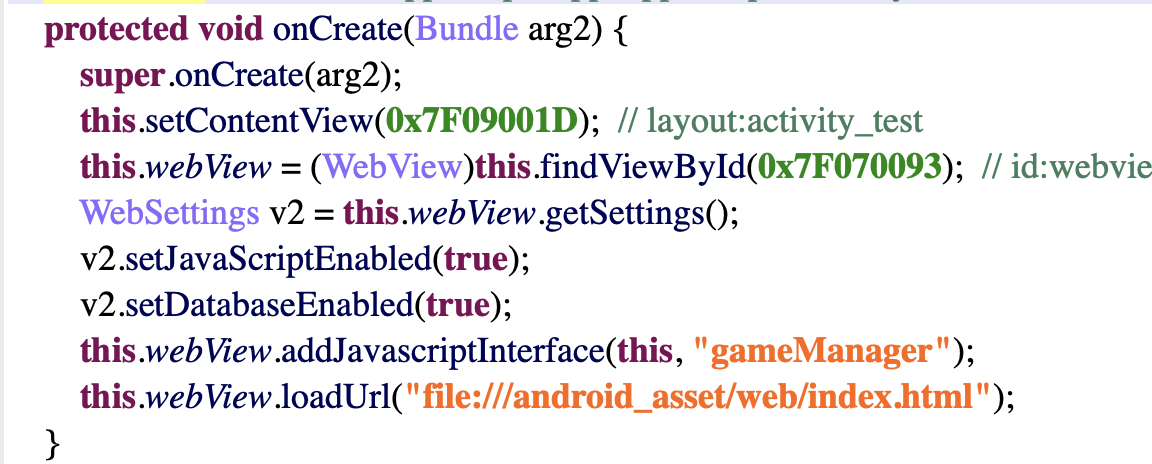
我们去assets下查看的时候会发现,其中game_manager.js被混淆,应该存在关键的逻辑,然后去分析Native文件。
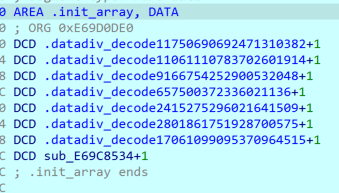
init_array有大量字符串解密,几乎有用的字符串都被加密了。
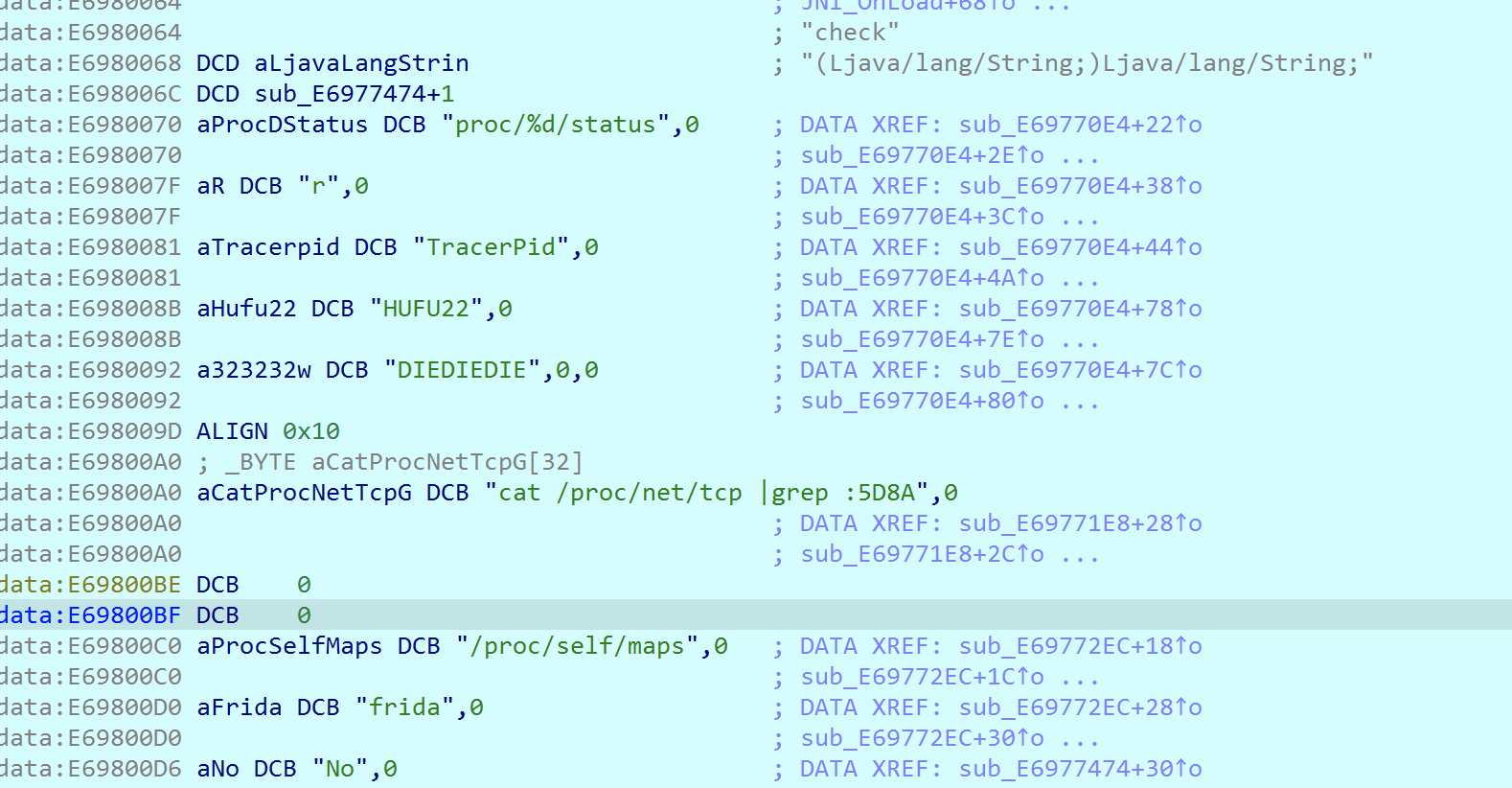
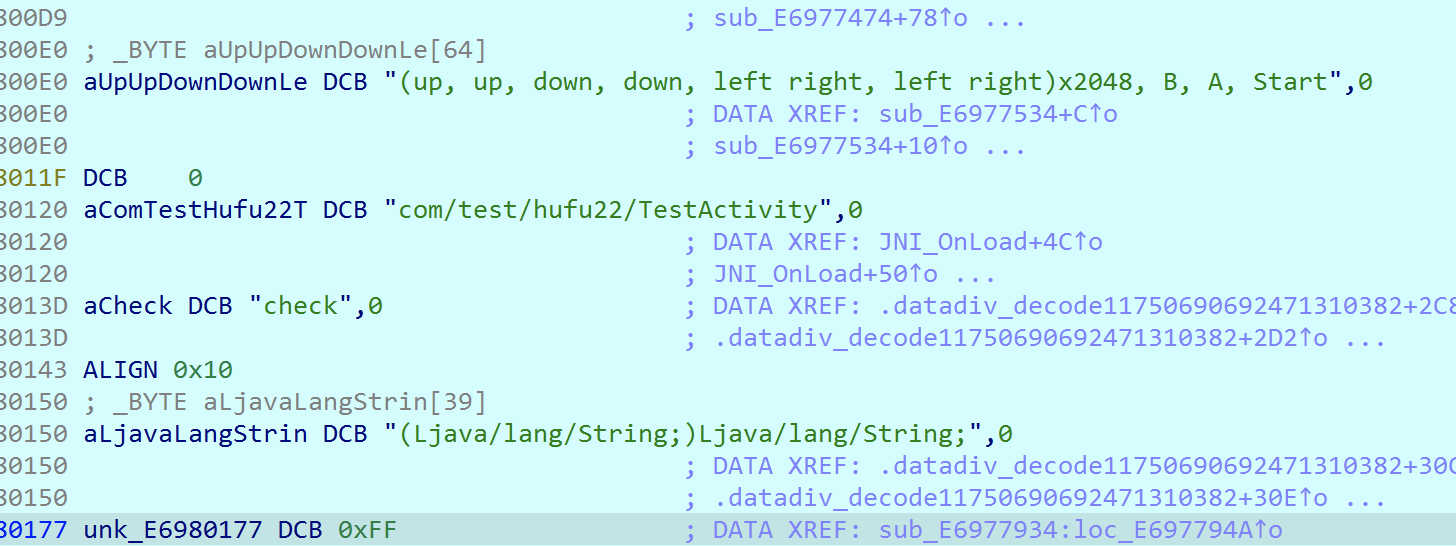
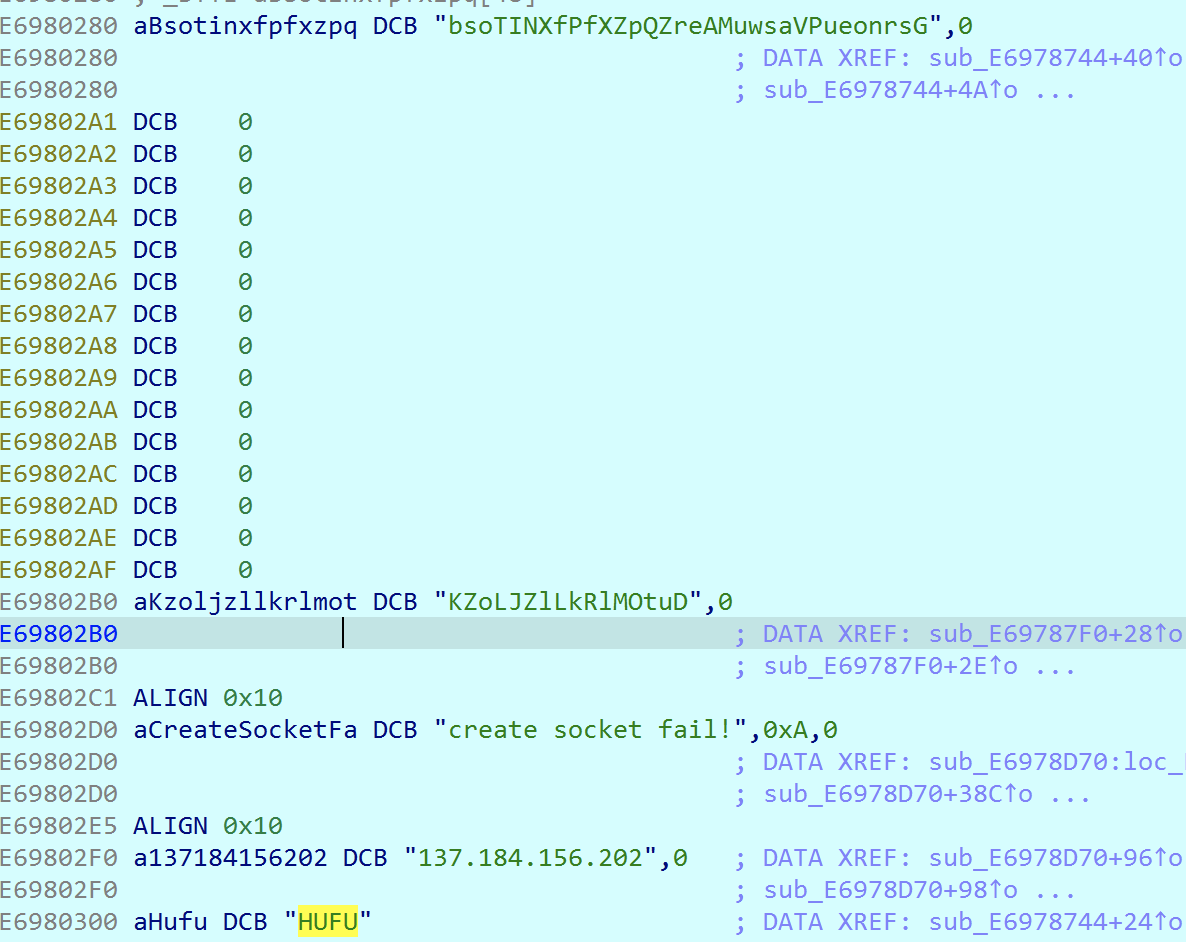
然后调用了一个函数,在so文件中存在多个类似的函数,是反调试,反Frida hook的,直接将这些调用全部Nop掉。之后进入JNI_OnLoad,动态注册了一个check函数,这里要经过init_array的字符串解密后才能看出来是check。
分析check函数:
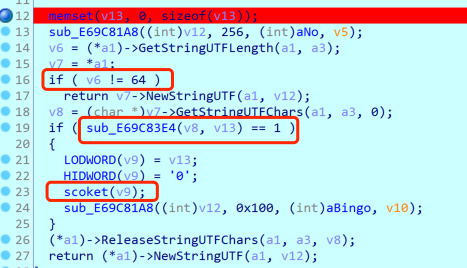
首先传入的参数的长度是64,然后调用了sub_E69C83E4,跟进分析:
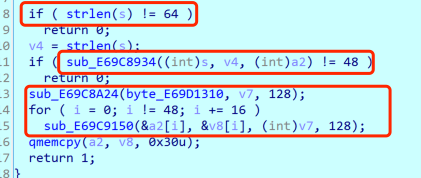
长度64字符串经过一个函数变为48,首先猜测是base64,虽然其中的编码表很奇怪。得到base64解密的结果,然后进行AES加密(S盒被修改了,当时就没注意),key就是这里的byte_E69D1310,它会被动态修改,后面会提到。做完这些工作之后,将AES加密的结果作为socket函数的参数(我修改了函数名为socket),跟进分析:
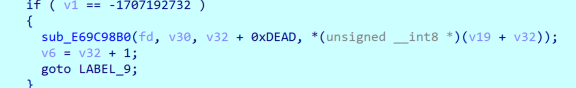
这里面有一些函数,会定义一个数据格式,然后使用sendto发送,也就是给的流量文件。大致的格式有如下两种:
1 | |
跟进上述函数进行分析:
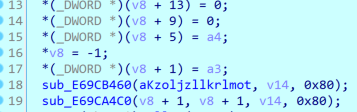
可以得知,strings2就是对第三个和第四个参数加密的结果,第三个参数是 i+0xdead,第四个参数是 *(i+v19),v19就是socket传入的参数。将数据包中的数据提取出来,对以下部分进行解密:
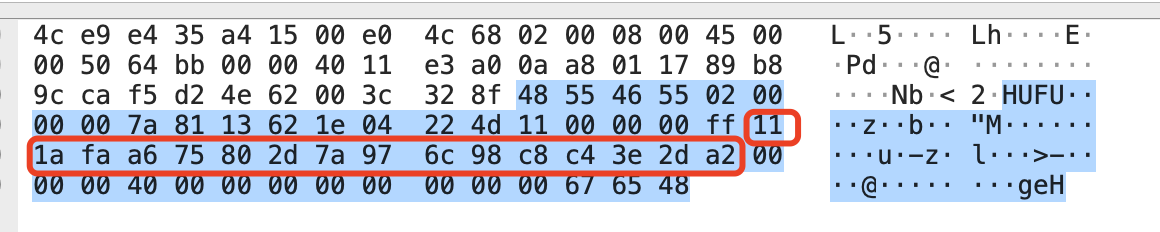
so文件我们分析的差不多了,接下来去分析JS代码,看到这混淆直接去世,使用这个网站能去一些混淆(https://deobfuscate.io/),但是其中有大量的base64字符串,分析前两个函数:
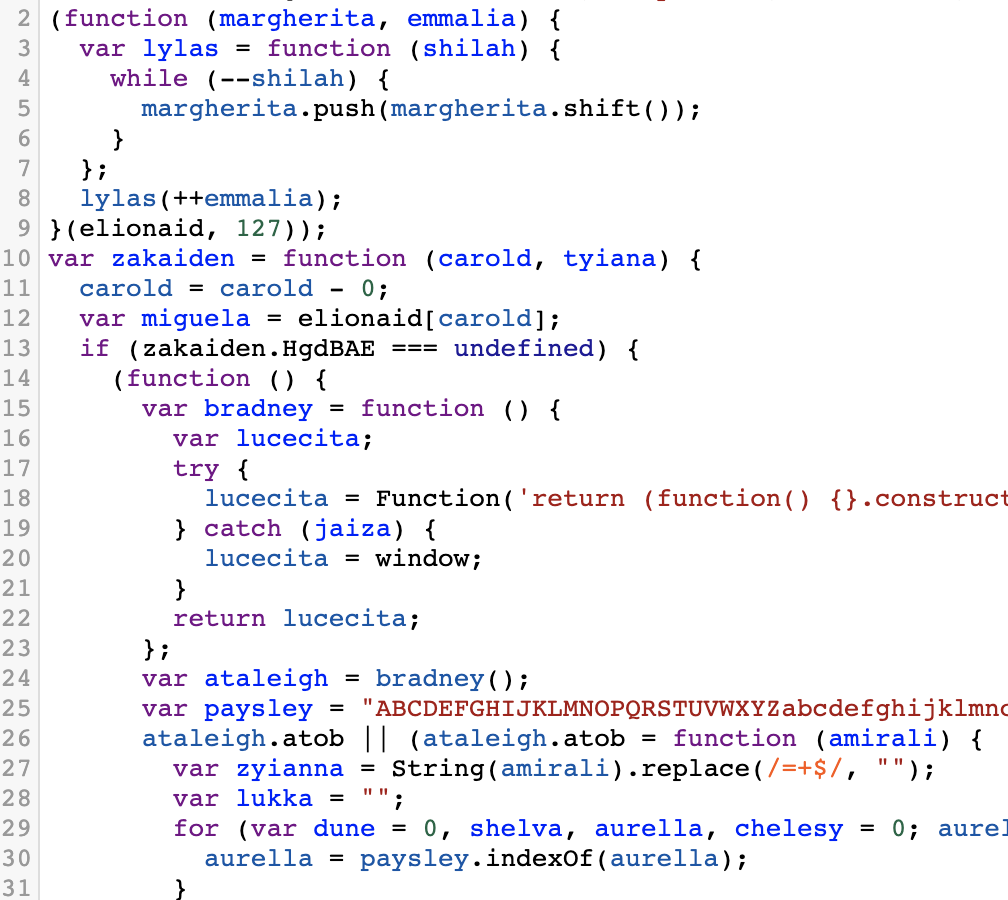
猜测作用应该是将开头的base64字符串数组进行顺序颠倒,然后base64解密,代码中会有大量的数组索引,我们对这些名称进行恢复,(使用网站每次反混淆后这个名称不固定):
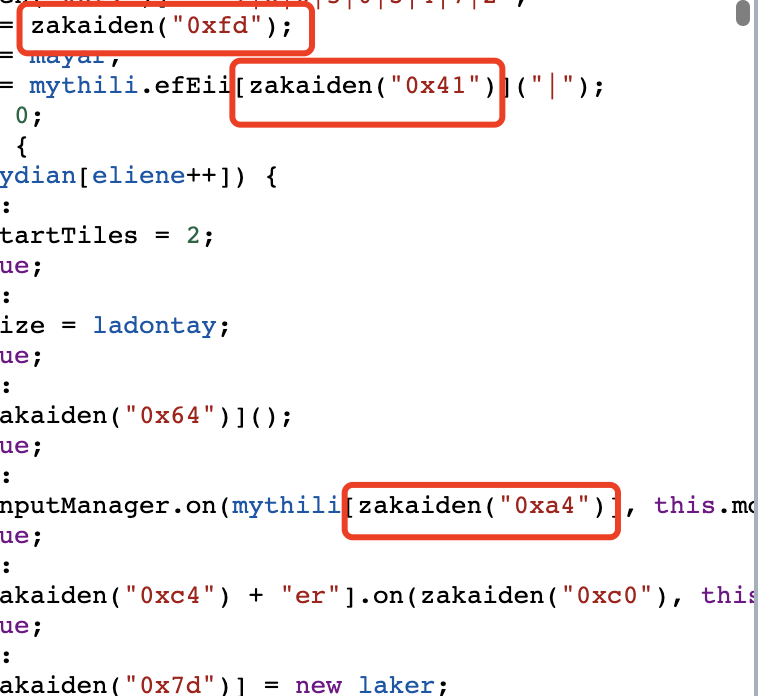
编写代码恢复函数名称,使用如下脚本可以恢复大多数函数,写的并不是很完美(会出现xxxx) + "xx"这种字符串),使用正则匹配可以更完善:
1 | |
解密之后先去找docheck,在GameManager.prototype.checkseq这个函数里调用了dockeck:
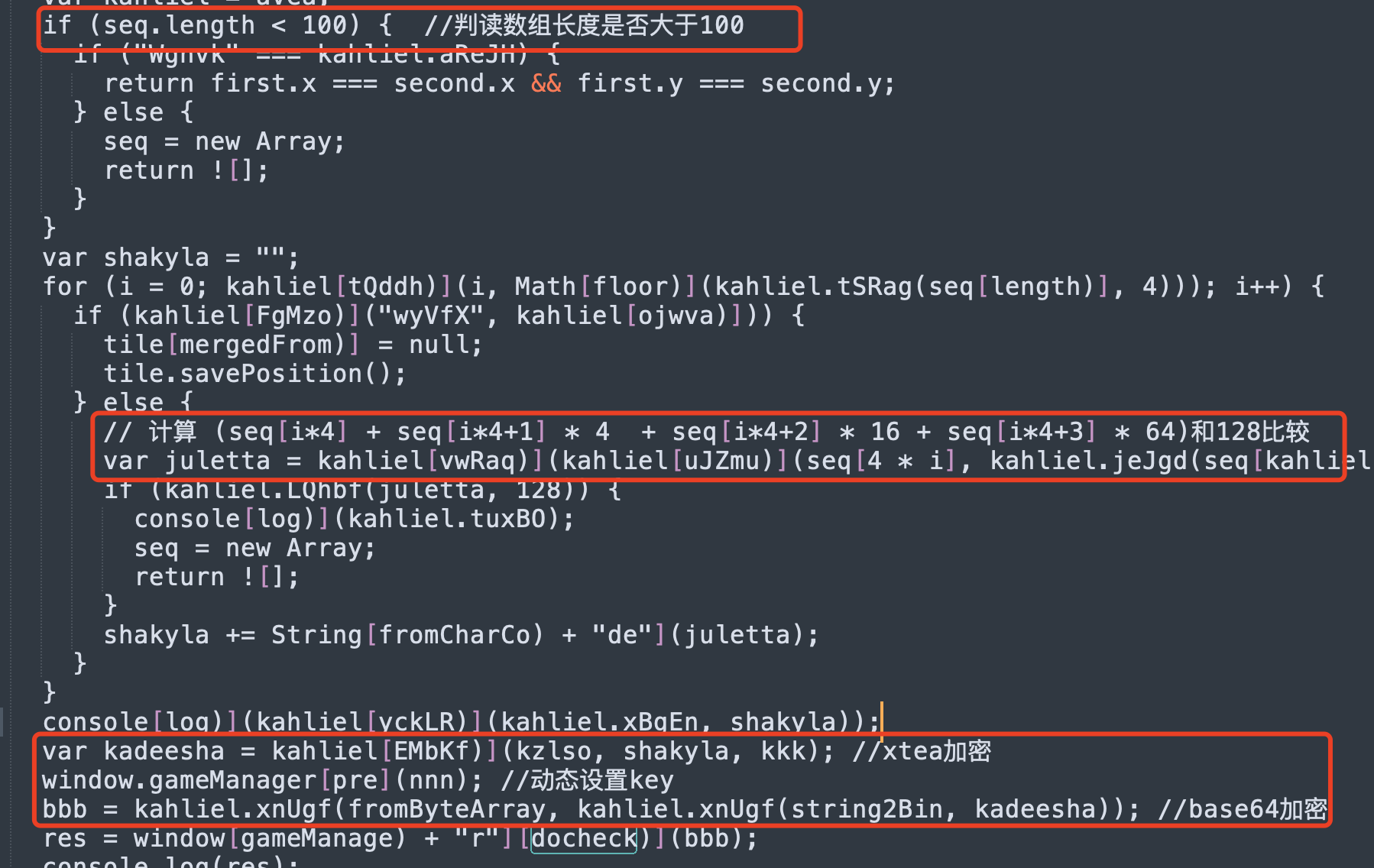
没有交叉引用,都是根据搜索字符串定位的。。。大致逻辑分析清楚了,只有seq长度大于100并且经过一个计算在128范围内才能调用docheck呢,并且会打印cheat code,我们再去看哪里调用了checkseq。
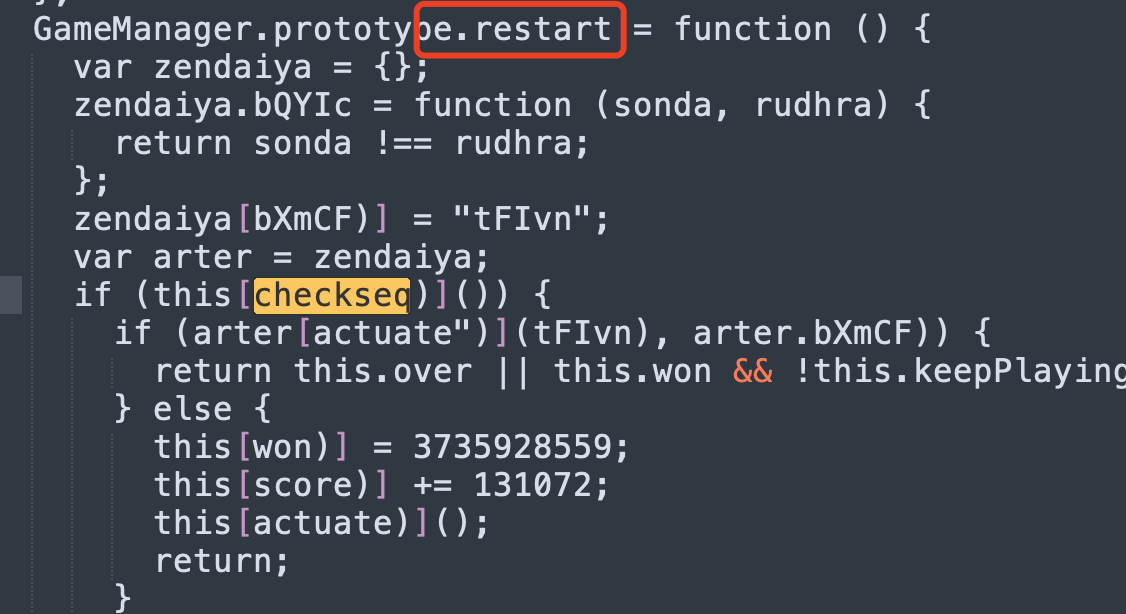
然后再搜索seq,看看seq怎么添加数据,在GameManager.prototype[move)]中发现,move可能就是滑动方块:
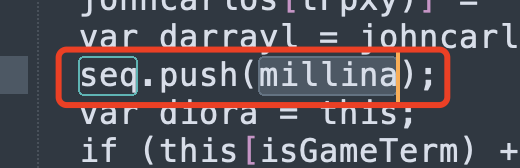
在跟踪move:
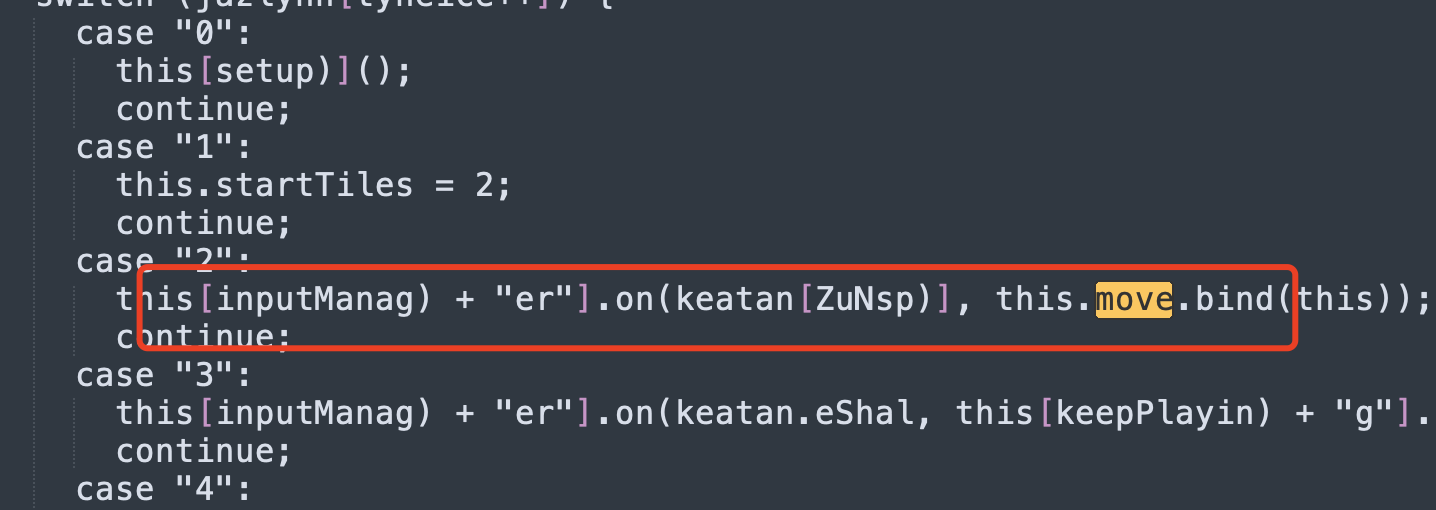
这里看到了inputmanager,我们在其他js文件里可以发现:
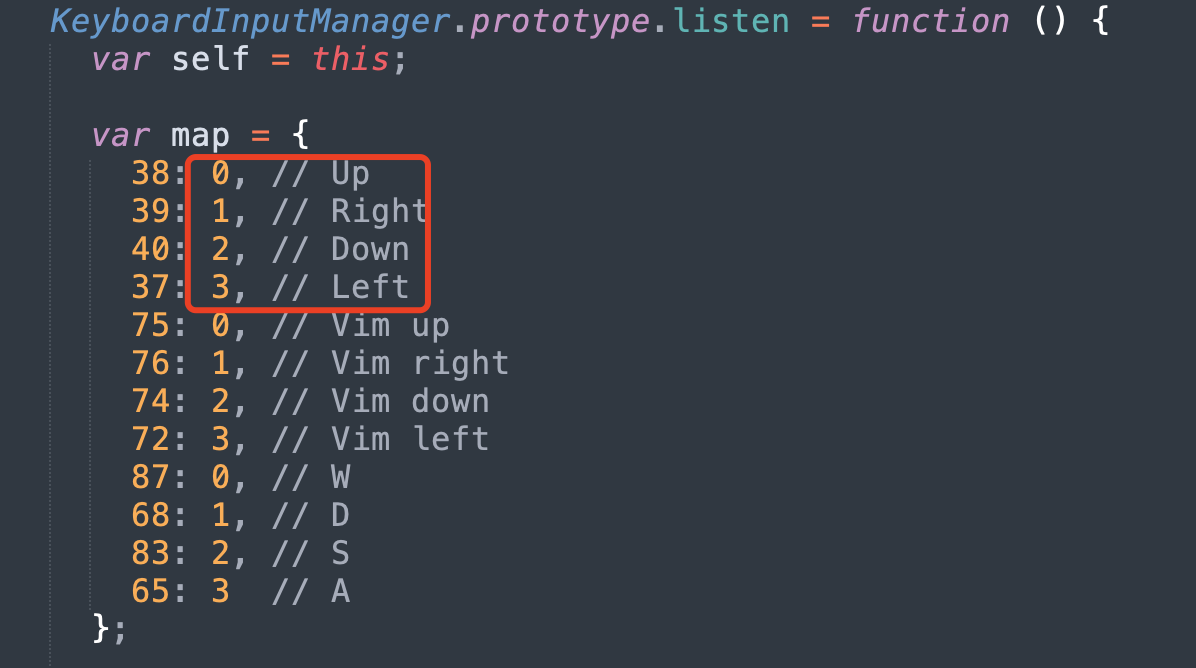
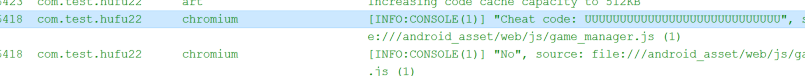
所以seq记录的是滑动的方向,我想了一下,这里必须是滑块移动才算数吗,然后我进行了100次右滑,点击newgame,成功输出cheat code,
1 | |
编写脚本解题,首先提取数据包中aes加密的数据:
1 | |
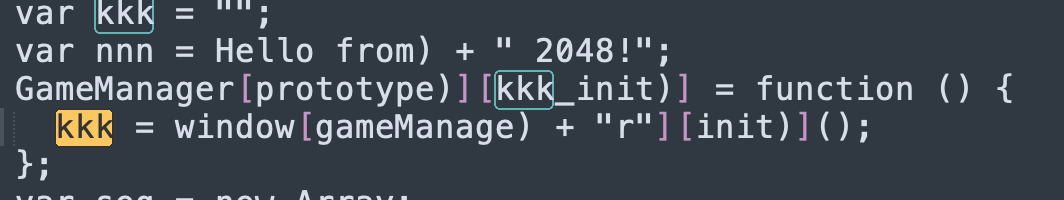
然后使用修改S盒的AES解密,解密代码太长不贴了,贴一个计算逆S盒,key是Hello from 2048!
1 | |
再进行Xtea解密,key是(up, up, down, d:
1 | |
解密即可得到flag。
fpbe
拿到题目分析了半天,发现要进行sha256爆破,但显然不可能,,然后去搜索这个bpf是什么东西,最后确定关键点。
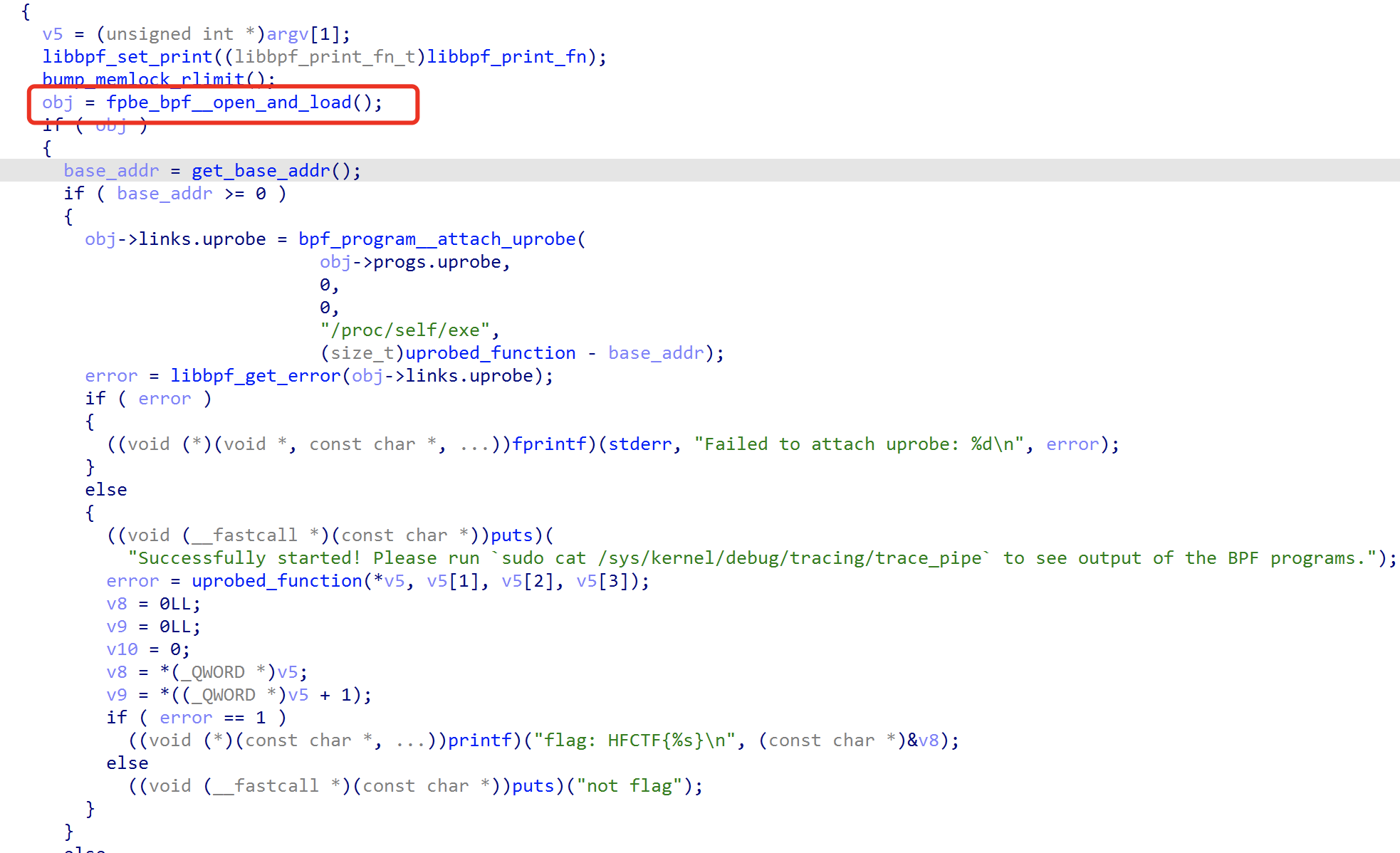
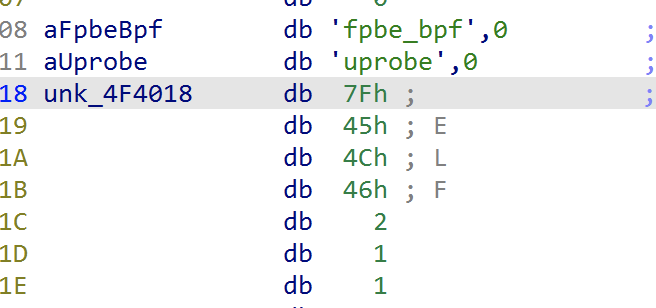
在这里面会加载一个bpf类的ELF文件,dump出来发现IDA也不解析,又去搜索反汇编,llvm-objdump就可以。
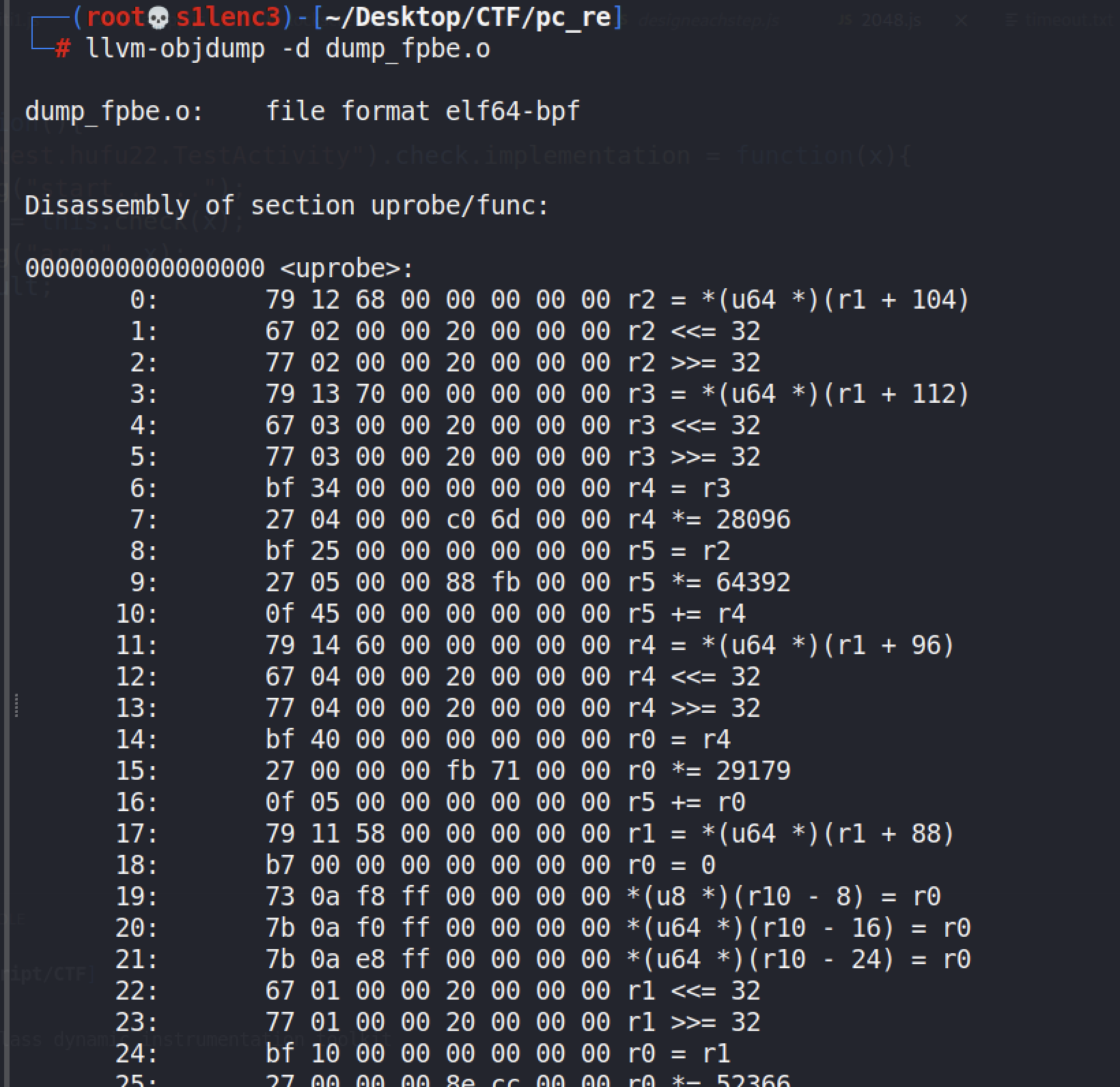
逻辑直接给了,解密即可,可用z3约束求解。
1 | |
the_shellcode
themida,也不会脱壳,废物一个。。。
开启两个进程,attach这两个进程,OD用于定位关键代码部分,结合OD定位的地址在ida中查看伪代码。
首先进行base64解密:
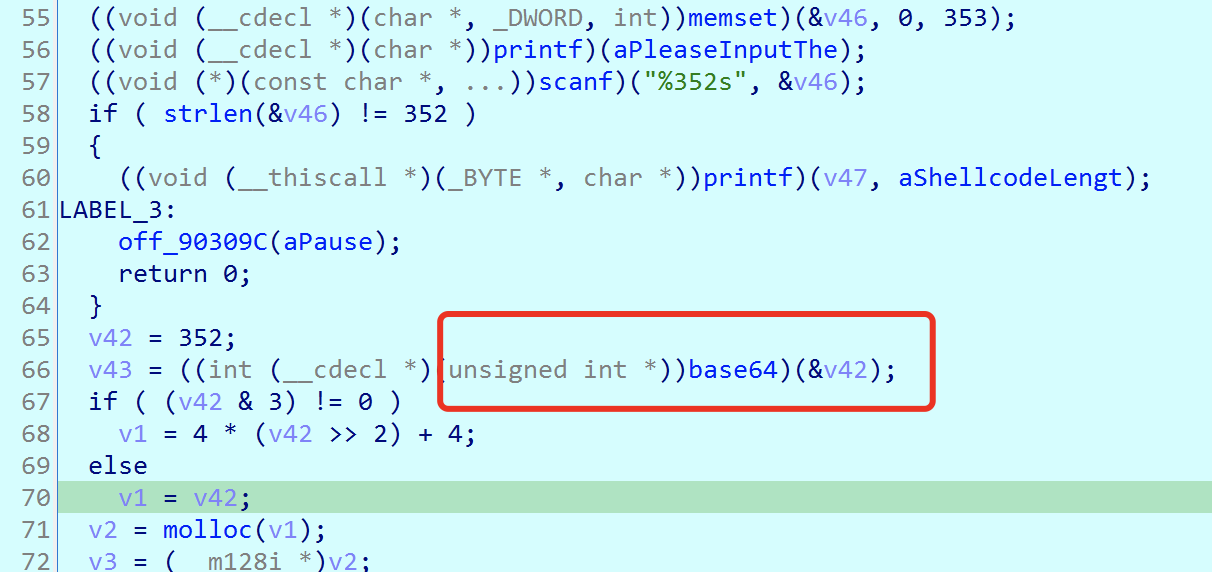
然后每个字符循环左移3bit,
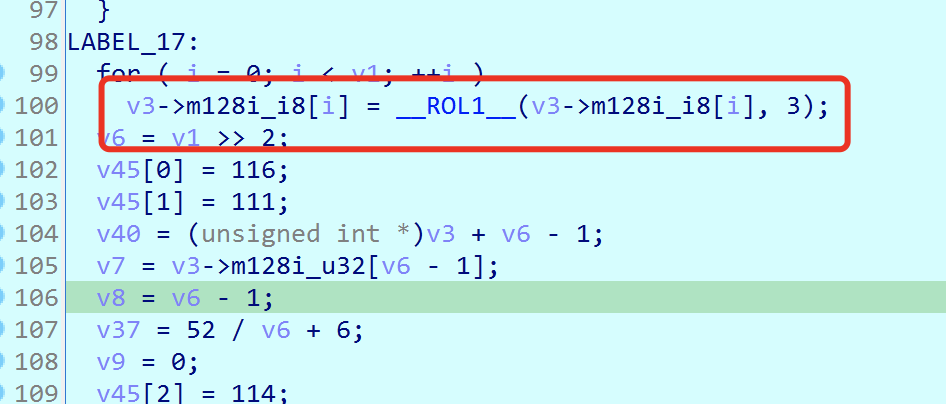
xxtea魔改加密:
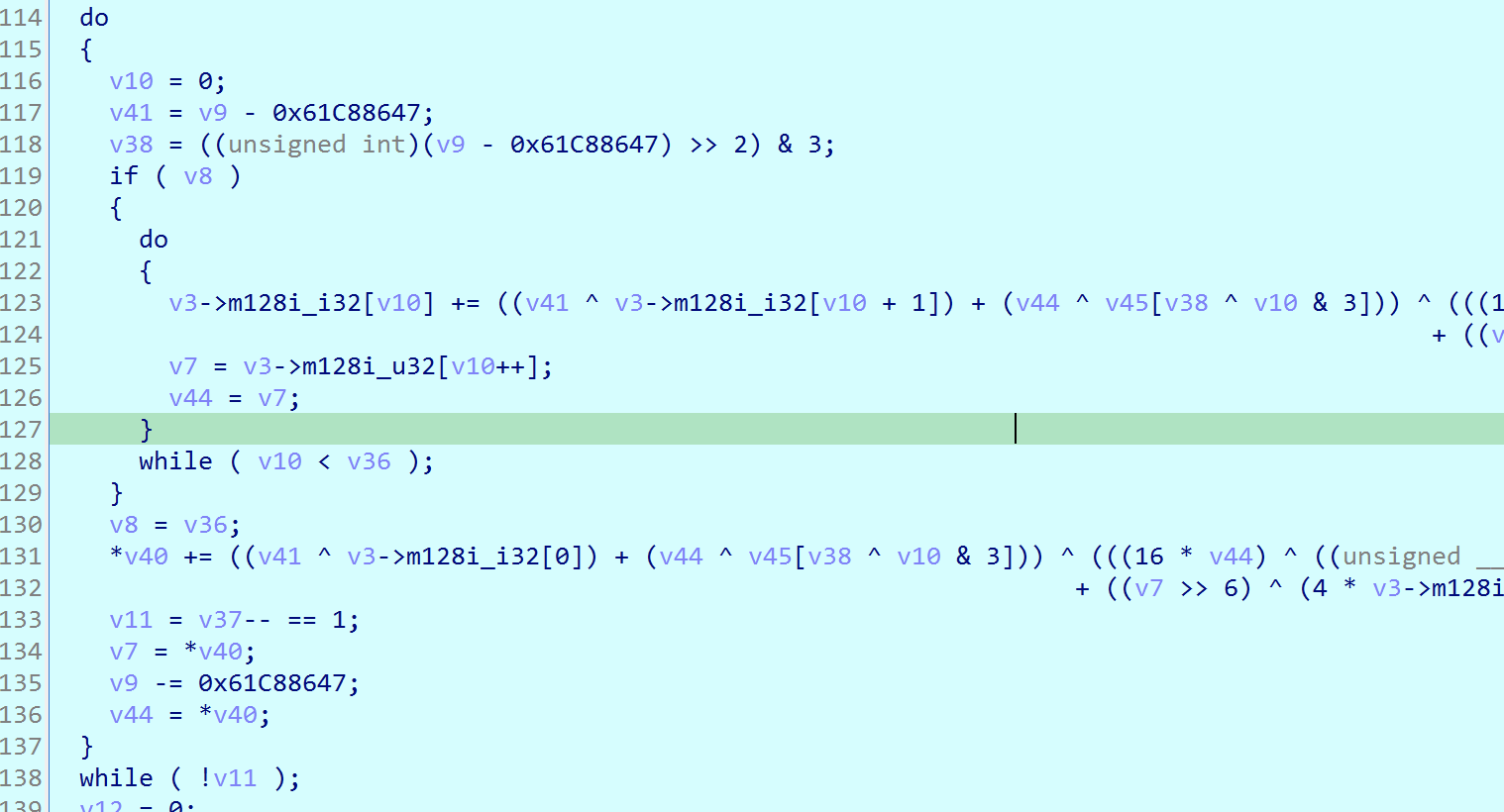
知道了加密过程,我们求解出shellcode:
1 | |
然后再加载shellcode:
1 | |
断点调试:
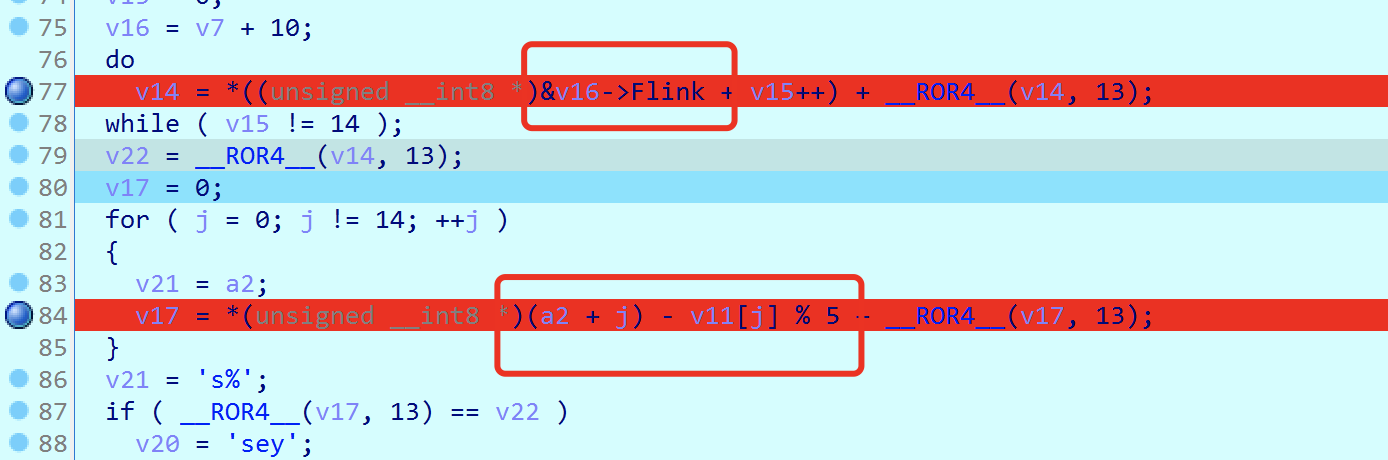
其实就是比较这两个,通过调试直接获取数据,解密:
1 | |
最后根据提示求md5即可:
1 | |
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!