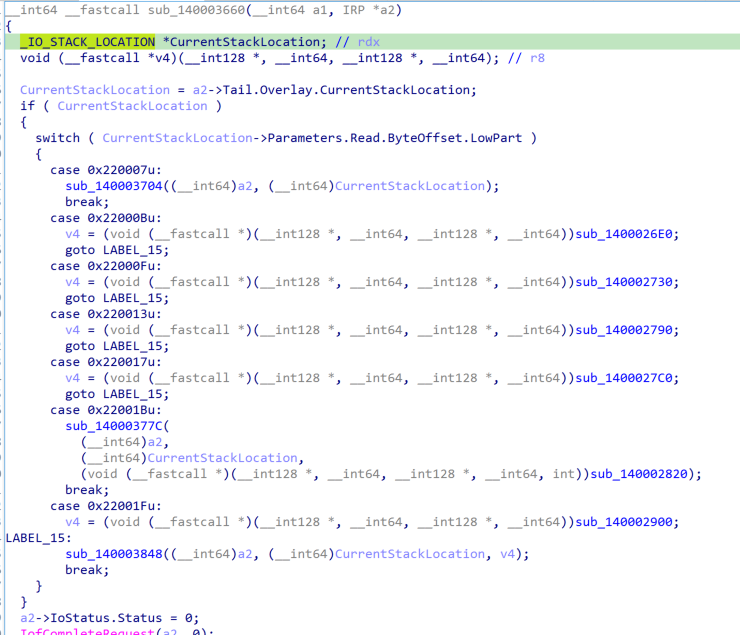
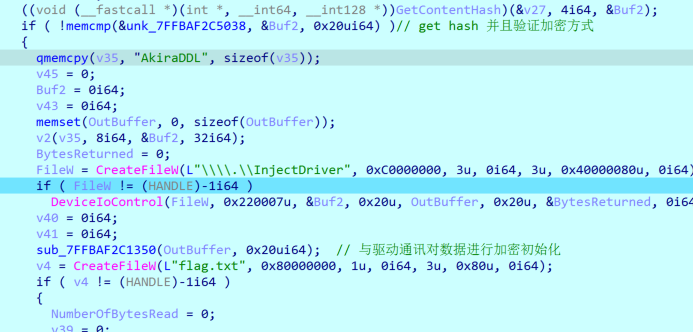
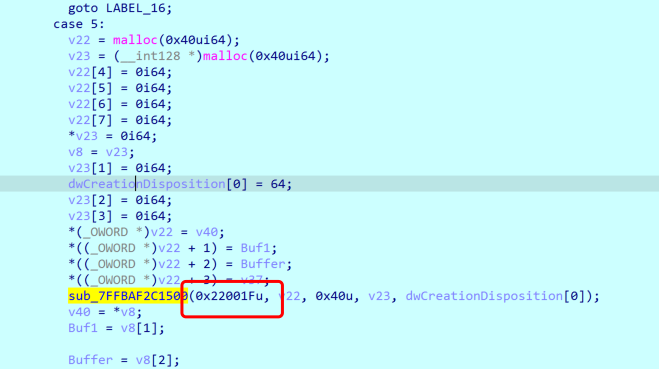
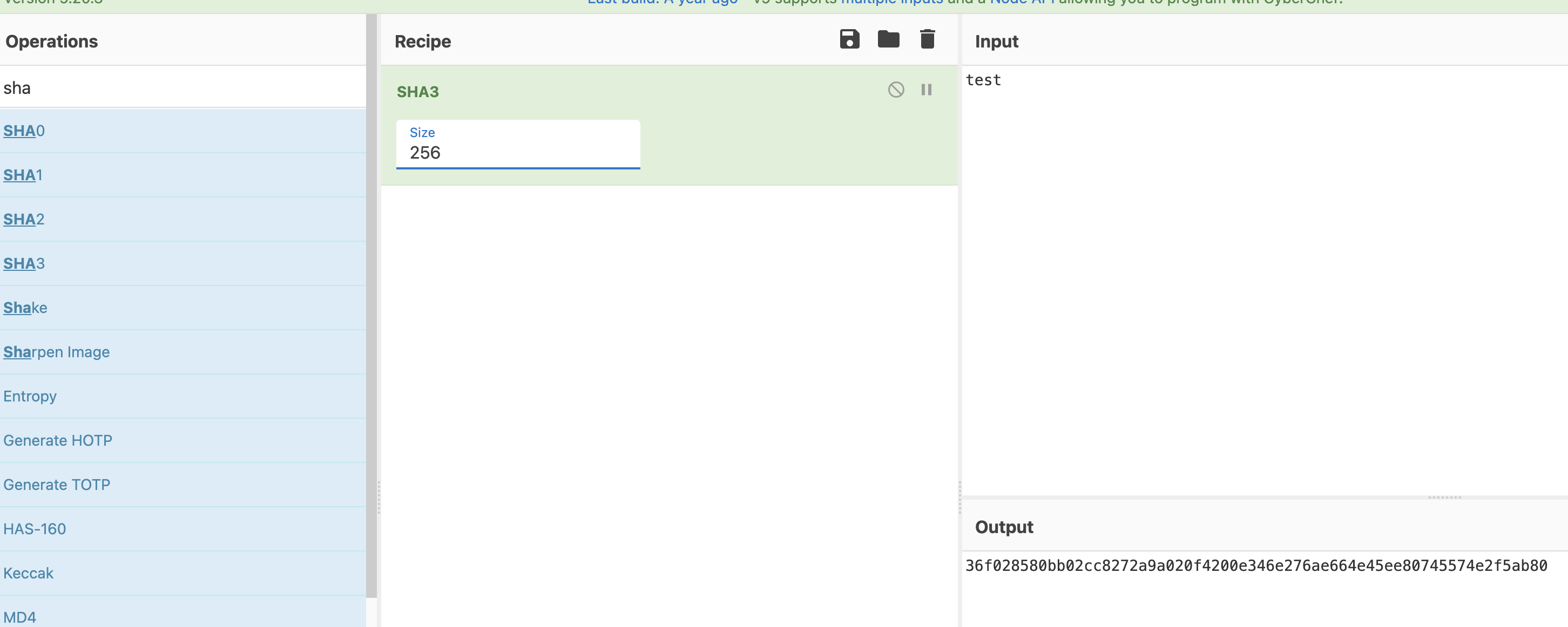
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
| from z3 import *
import ctypes
key = []
s1 = [0xA5, 0xCF, 0xCD, 0xD6, 0xC5, 0xC3, 0xB1, 0xC5, 0xD2, 0xD9, 0xD7, 0xC7, 0xD6, 0xCD, 0xD4, 0xD8, 0xC3, 0xBB, 0xCD, 0xD8, 0xCC, 0xC3, 0xB0, 0xC5, 0xD8, 0xC9, 0xDC, 0x00, 0x00, 0x00, 0x00, 0x00]
for i in range(32):
s = 0
for j in range(i+1):
s ^= s1[j]
key.append(s)
print(key)
item = [5, 5, 4, 4, 5, 4, 0, 0, 4, 2, 5, 5, 1, 3, 1, 5, 1, 2, 3, 0, 3, 0, 2, 3, 4, 4, 3, 2, 2, 5, 5, 0]
cmp = [0x57, 0xc5, 0x38, 0x1b, 0x3a, 0xa8, 0x34, 0x2f, 0x39, 0x97, 0xc6, 0xe4, 0x04, 0x2f, 0x8f, 0xee, 0x5e, 0x51, 0x80, 0x67, 0x24, 0xc9, 0x6f, 0x48, 0x5b, 0x7f, 0xbd, 0xc7, 0xb0, 0xc2, 0xc2, 0xeb]
def _22000b():
for i in range(32):
key[i] = (key[i] + 16) & 0xff
inp[i] ^= key[i]
def _22000f():
for i in range(32):
key[i] = (key[i] - 80) & 0xff
tmp = ((key[i] << 4) & 0xf0) | ((key[i] >> 4) & 0x0f)
inp[i] ^= tmp
def _220013():
for i in range(32):
inp[i] ^= key[i]
def _220017():
for i in range(32):
key[i] = (key[i] - 80) & 0xff
for j in range(16):
inp[j*2] ^= (key[j*2] << 4) & 0xff
inp[j*2+1] ^= (key[j*2] >> 4) & 0x0f
def _22001b():
for j in range(32):
inp[j] ^= key[j]
def _22001f():
for i in range(32):
if ctypes.c_uint8(key[i] - 33).value > 46:
if ctypes.c_uint8(key[i] - 81).value > 46:
if key[i] > 0x80:
key[i] -= 48
inp[i] = ((inp[i] - key[i]) & 0xff)
else:
key[i] -= 48
inp[i] = (inp[i] ^ (key[i] >> 4)) & 0xff
else:
key[i] = (key[i] - 80) & 0xff
inp[i] = (inp[i] + key[i]) & 0xff
s = Solver()
inp = [BitVec("x%s" % i, 32) for i in range(32)]
for i in range(32):
if item[i] == 0:
_22000b()
if item[i] == 1:
_22000f()
if item[i] == 2:
_220013()
if item[i] == 3:
_220017()
if item[i] == 4:
_22001b()
if item[i] == 5:
_22001f()
for i in range(32):
s.add(inp[i] & 0xff == cmp[i])
x = [BitVec("x%s" % i, 32) for i in range(32)]
if (s.check() == sat):
model = s.model()
print(model)
flag=""
for i in range(32):
if (model[x[i]] != None):
flag += chr(model[x[i]].as_long().real)
else:
flag += " "
print('"' + flag + '"')
|